Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence). A person who commits espionage is called an espionage agent or spy. Any individual or spy ring, in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law.
The technological singularity—or simply the singularity—is a hypothetical future point in time at which technological growth becomes uncontrollable and irreversible, resulting in unforeseeable changes to human civilization. According to the most popular version of the singularity hypothesis, I.J. Good's intelligence explosion model, an upgradable intelligent agent will eventually enter a "runaway reaction" of self-improvement cycles, each new and more intelligent generation appearing more and more rapidly, causing an "explosion" in intelligence and resulting in a powerful superintelligence that qualitatively far surpasses all human intelligence.

The Defense Intelligence Agency (DIA) is an intelligence agency and combat support agency of the United States Department of Defense, specializing in defense and military intelligence.

Military intelligence is a military discipline that uses information collection and analysis approaches to provide guidance and direction to assist commanders in their decisions. This aim is achieved by providing an assessment of data from a range of sources, directed towards the commanders' mission requirements or responding to questions as part of operational or campaign planning. To provide an analysis, the commander's information requirements are first identified, which are then incorporated into intelligence collection, analysis, and dissemination.

Counterintelligence is an activity aimed at protecting an agency's intelligence program from an opposition's intelligence service. It includes gathering information and conducting activities to prevent espionage, sabotage, assassinations or other intelligence activities conducted by, for, or on behalf of foreign powers, organizations or persons.
Measurement and signature intelligence (MASINT) is a technical branch of intelligence gathering, which serves to detect, track, identify or describe the distinctive characteristics (signatures) of fixed or dynamic target sources. This often includes radar intelligence, acoustic intelligence, nuclear intelligence, and chemical and biological intelligence. MASINT is defined as scientific and technical intelligence derived from the analysis of data obtained from sensing instruments for the purpose of identifying any distinctive features associated with the source, emitter or sender, to facilitate the latter's measurement and identification.
An intelligence officer is a person employed by an organization to collect, compile or analyze information which is of use to that organization. The word of officer is a working title, not a rank, used in the same way a "police officer" can also be a sergeant, or in the military, in which non-commissioned personnel may serve as intelligence officers.
In intelligence organizations, agent handling is the management of so-called agents, principal agents, and agent networks by intelligence officers typically known as case officers.
The Intelligence cycle describes how intelligence is ideally processed in civilian and military intelligence agencies, and law enforcement organizations. It is a closed path consisting of repeating nodes, which will result in finished intelligence. The stages of the intelligence cycle include the issuance of requirements by decision makers, collection, processing, analysis, and publication of intelligence. The circuit is completed when decision makers provide feedback and revised requirements. The intelligence cycle is also called the Intelligence Process by the U.S. Department of Defense (DoD) and the uniformed services.
The Joint Functional Component Command for Intelligence, Surveillance and Reconnaissance was a subordinate command of the United States Strategic Command, one of the nine Unified Combatant Commands under the United States Department of Defense (DOD) and co-located with the Defense Intelligence Agency (DIA). It served as the center for planning, execution and assessment of the United States military's global Intelligence, Surveillance, and Reconnaissance operations from 2005-2016; a key enabler to achieving global situational awareness. In 2016 JFCC-ISR was realigned to the Joint Staff.

The Directorate of Operations (DO), less formally called the Clandestine Service, is a component of the US Central Intelligence Agency. It was known as the Directorate of Plans from 1951 to 1973; as the Directorate of Operations from 1973 to 2005; and as the National Clandestine Service (NCS) from 2005 to 2015.
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberately deceptive information; the analyst must correlate the similarities among deceptions and extract a common truth. Although its practice is found in its purest form inside national intelligence agencies, its methods are also applicable in fields such as business intelligence or competitive intelligence.
Intelligence collection management is the process of managing and organizing the collection of intelligence from various sources. The collection department of an intelligence organization may attempt basic validation of what it collects, but is not supposed to analyze its significance. There is debate in U.S. intelligence community on the difference between validation and analysis, where the National Security Agency may try to interpret information when such interpretation is the job of another agency.
Intelligence cycle management refers to the overall activity of guiding the intelligence cycle, which is a set of processes used to provide decision-useful information (intelligence) to leaders. The cycle consists of several processes, including planning and direction, collection, processing and exploitation, analysis and production, and dissemination and integration. The related field of counterintelligence is tasked with impeding the intelligence efforts of others. Intelligence organizations are not infallible but, when properly managed and tasked, can be among the most valuable tools of management and government.
National intelligence programs, and, by extension, the overall defenses of nations, are vulnerable to attack. It is the role of intelligence cycle security to protect the process embodied in the intelligence cycle, and that which it defends. A number of disciplines go into protecting the intelligence cycle. One of the challenges is there are a wide range of potential threats, so threat assessment, if complete, is a complex task. Governments try to protect three things:
The target-centric approach to intelligence is a method of intelligence analysis that Robert M. Clark introduced in his book "Intelligence Analysis: A Target-Centric Approach" in 2003 to offer an alternative methodology to the traditional intelligence cycle. Its goal is to redefine the intelligence process in such a way that all of the parts of the intelligence cycle come together as a network. It is a collaborative process where collectors, analysts and customers are integral, and information does not always flow linearly.
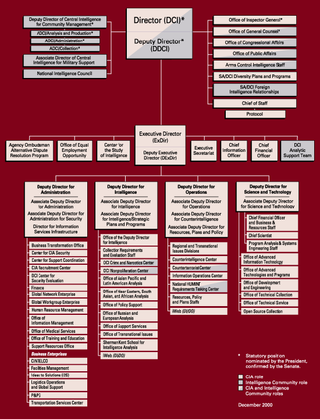
The CIA publishes organizational charts of its agency. Here are a few examples.
CyberHumint refers to the set of skills used by hackers, within Cyberspace, in order to obtain private information while attacking the human factor, using various psychological deceptions. CyberHumint includes the use of traditional human espionage methodologies, such as agent recruitment, information gathering through deception, traditionally known as Humint, combined with deception technologies known as Social engineering.

The Intelligence Regiment is a regiment of the Royal Danish Army. It was originally created as the Army Intelligence Centre, and was a collection of all intelligence units, created by the Danish Defence Agreement 2013-2017 on the basis of lessons learned in Afghanistan and Iraq. Following the Danish Defence Agreement 2018–23, the centre was upgraded to a regiment and the name was changed.





