Related Research Articles
In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks, with an unvarying transformation that is specified by a symmetric key. Block ciphers operate as important elementary components in the design of many cryptographic protocols, and are widely used to implement encryption of bulk data.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in information input can affect the resultant difference at the output. In the case of a block cipher, it refers to a set of techniques for tracing differences through the network of transformation, discovering where the cipher exhibits non-random behavior, and exploiting such properties to recover the secret key.
Eli Biham is an Israeli cryptographer and cryptanalyst, currently a professor at the Technion - Israel Institute of Technology Computer Science department. Starting from October 2008 and till 2013, Biham was the dean of the Technion Computer Science department, after serving for two years as chief of CS graduate school. Biham received his Ph.D. for inventing (publicly) differential cryptanalysis, while working under Adi Shamir. It had, it turned out, been invented at least twice before. A team at IBM discovered it during their work on DES, and was requested/required to keep their discovery secret by the NSA, who evidently knew about it as well.
In cryptography, Lucifer was the name given to several of the earliest civilian block ciphers, developed by Horst Feistel and his colleagues at IBM. Lucifer was a direct precursor to the Data Encryption Standard. One version, alternatively named DTD-1, saw commercial use in the 1970s for electronic banking.
Snefru is a cryptographic hash function invented by Ralph Merkle in 1990 while working at Xerox PARC. The function supports 128-bit and 256-bit output. It was named after the Egyptian Pharaoh Sneferu, continuing the tradition of the Khufu and Khafre block ciphers.
In cryptography, Skipjack is a block cipher—an algorithm for encryption—developed by the U.S. National Security Agency (NSA). Initially classified, it was originally intended for use in the controversial Clipper chip. Subsequently, the algorithm was declassified.

The GOST block cipher (Magma), defined in the standard GOST 28147-89, is a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard, GOST R 34.12-2015, specifies that it may be referred to as Magma. The GOST hash function is based on this cipher. The new standard also specifies a new 128-bit block cipher called Kuznyechik.
In cryptography, Tiger is a cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits. Truncated versions can be used for compatibility with protocols assuming a particular hash size. Unlike the SHA-2 family, no distinguishing initialization values are defined; they are simply prefixes of the full Tiger/192 hash value.
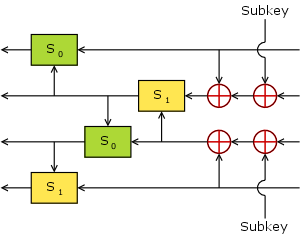
In cryptography, FEAL is a block cipher proposed as an alternative to the Data Encryption Standard (DES), and designed to be much faster in software. The Feistel based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT. The cipher is susceptible to various forms of cryptanalysis, and has acted as a catalyst in the discovery of differential and linear cryptanalysis.
In cryptography, the Generalized DES Scheme is a variant of the DES symmetric-key block cipher designed with the intention of speeding up the encryption process while improving its security. The scheme was proposed by Ingrid Schaumuller-Bichl in 1981.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
In cryptography, LOKI89 and LOKI91 are symmetric-key block ciphers designed as possible replacements for the Data Encryption Standard (DES). The ciphers were developed based on a body of work analysing DES, and are very similar to DES in structure. The LOKI algorithms were named for Loki, the god of mischief in Norse mythology.
In cryptography, REDOC II and REDOC III are block ciphers designed by Michael Wood (cryptographer) for Cryptech Inc and are optimised for use in software. Both REDOC ciphers are patented.
In cryptography, impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences that propagate through the cipher with greater than expected probability, impossible differential cryptanalysis exploits differences that are impossible at some intermediate state of the cipher algorithm.
In cryptography, Nimbus is a block cipher invented by Alexis Machado in 2000. It was submitted to the NESSIE project, but was not selected.
In cryptography, Q is a block cipher invented by Leslie McBride. It was submitted to the NESSIE project, but was not selected.
Alex Biryukov is a cryptographer, currently a full professor at the University of Luxembourg. His notable work includes the design of the stream cipher LEX, as well as the cryptanalysis of numerous cryptographic primitives. In 1998, he developed impossible differential cryptanalysis together with Eli Biham and Adi Shamir. In 1999, he developed the slide attack together with David Wagner. In 2009 he developed, together with Dmitry Khovratovich, the first cryptanalytic attack on full-round AES-192 and AES-256 that is faster than a brute-force attack. In 2015 he developed the Argon2 key derivation function with Daniel Dinu and Dmitry Khovratovich. Since 1994 Alex Biryukov is a member of the International Association for Cryptologic Research.
In cryptography, COCONUT98 is a block cipher designed by Serge Vaudenay in 1998. It was one of the first concrete applications of Vaudenay's decorrelation theory, designed to be provably secure against differential cryptanalysis, linear cryptanalysis, and even certain types of undiscovered cryptanalytic attacks.
This article summarizes publicly known attacks against block ciphers and stream ciphers. Note that there are perhaps attacks that are not publicly known, and not all entries may be up to date.
References
- Eli Biham, Adi Shamir (1991). "Differential Cryptanalysis of Feal and N-Hash". EUROCRYPT . Lecture Notes in Computer Science. 547: 1–16. doi:10.1007/3-540-46416-6_1. ISBN 978-3-540-54620-7.CS1 maint: uses authors parameter (link)
- S. Miyaguchi, K. Ohta, and M. Iwata (November 1990). "128-bit hash function (N-hash)". NTT Review. 2 (6): 128–132.CS1 maint: uses authors parameter (link)
| This cryptography-related article is a stub. You can help Wikipedia by expanding it. |