
Internet Explorer is a retired series of graphical web browsers developed by Microsoft that were used in the Windows line of operating systems. While IE has been discontinued on most Windows editions, it remains supported on certain editions of Windows, such as Windows 10 LTSB/LTSC. Starting in 1995, it was first released as part of the add-on package Plus! for Windows 95 that year. Later versions were available as free downloads or in-service packs and included in the original equipment manufacturer (OEM) service releases of Windows 95 and later versions of Windows. Microsoft spent over US$100 million per year on Internet Explorer in the late 1990s, with over 1,000 people involved in the project by 1999. New feature development for the browser was discontinued in 2016 and ended support on June 15, 2022 for Windows 10 Semi-Annual Channel (SAC), in favor of its successor, Microsoft Edge.
Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and has a specialized meaning that is distinct from the field of confidential computing. With Trusted Computing, the computer will consistently behave in expected ways, and those behaviors will be enforced by computer hardware and software. Enforcing this behavior is achieved by loading the hardware with a unique encryption key that is inaccessible to the rest of the system and the owner.

The Next-Generation Secure Computing Base is a software architecture designed by Microsoft which claimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed platforms such as set-top boxes while simultaneously preserving the backward compatibility, flexibility, and openness of the Windows operating system. Microsoft's primary stated objective with NGSCB was to "protect software from software."
In computing, Download.ject is a malware program for Microsoft Windows servers. When installed on an insecure website running on Microsoft Internet Information Services (IIS), it appends malicious JavaScript to all pages served by the site.

Microsoft Defender Antivirus is an antivirus software component of Microsoft Windows. It was first released as a downloadable free anti-spyware program for Windows XP and was shipped with Windows Vista and Windows 7. It has evolved into a full antivirus program, replacing Microsoft Security Essentials in Windows 8 or later versions.

Windows Internet Explorer 7 (IE7) is a web browser for Windows. It was released by Microsoft on October 18, 2006, as the seventh version of Internet Explorer and the successor to Internet Explorer 6. Internet Explorer 7 is part of a long line of versions of Internet Explorer and was the first major update to the browser since 2001. It was the default browser in Windows Vista and Windows Server 2008, as well as Windows Embedded POSReady 2009, and can replace Internet Explorer 6 on Windows XP and Windows Server 2003, but unlike version 6, this version does not support Windows 2000, Windows ME, or earlier versions of Windows. It also does not support Windows 7, Windows Server 2008 R2 or later Windows Versions.

Microsoft developed 11 versions of Internet Explorer for Windows from 1995 to 2013. Microsoft also developed Internet Explorer for Mac, Internet Explorer for UNIX, and Internet Explorer Mobile respectively for Apple Macintosh, Unix, and mobile devices; the first two are discontinued but the latter runs on Windows CE, Windows Mobile, and Windows Phone.

Windows Vista is a major release of Microsoft's Windows NT operating system. It was released to manufacturing on November 8, 2006, and became generally available on January 30, 2007, on the Windows Marketplace, the first release of Windows to be made available through a digital distribution platform. Vista succeeded Windows XP (2001); at the time, the five-year gap between the two was the longest time span between successive Windows releases.
Criticism of Windows XP deals with issues with security, performance and the presence of product activation errors that are specific to the Microsoft operating system Windows XP.
There are a number of security and safety features new to Windows Vista, most of which are not available in any prior Microsoft Windows operating system release.
Windows Vista, an operating system released by Microsoft for consumers on January 30, 2007, has been widely criticized by reviewers and users. Due to issues with new security features, performance, driver support and product activation, Windows Vista has been the subject of a number of negative assessments by various groups.
The Protected Media Path is a set of technologies creating a "Protected Environment," first included in Microsoft's Windows Vista operating system, that is used to enforce digital rights management protections on content. Its subsets are Protected Video Path (PVP) and Protected User Mode Audio (PUMA). Any application that uses Protected Media Path in Windows uses Media Foundation.
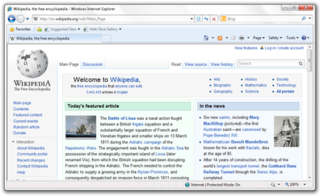
Windows Internet Explorer 8 (IE8) is the eighth and, by now, discontinued version of the Internet Explorer web browser for Windows. It was released by Microsoft on March 19, 2009, as the successor to Internet Explorer 7. It was the default browser in Windows 7 and Windows Server 2008 R2.

Peter Claus Gutmann is a computer scientist in the Department of Computer Science at the University of Auckland, Auckland, New Zealand. He has a Ph.D. in computer science from the University of Auckland. His Ph.D. thesis and a book based on the thesis were about a cryptographic security architecture. He is interested in computer security issues, including security architecture, security usability, and hardware security; he has discovered several flaws in publicly released cryptosystems and protocols. He is the developer of the cryptlib open source software security library and contributed to PGP version 2. In 1994 he developed the Secure FileSystem (SFS). He is also known for his analysis of data deletion on electronic memory media, magnetic and otherwise, and devised the Gutmann method for erasing data from a hard drive more or less securely. Having lived in New Zealand for some time, he has written on such subjects as weta, and the Auckland power crisis of 1998, during which the electrical power system failed completely in the central city for five weeks, which he has blogged about. He has also written on his career as an "arms courier" for New Zealand, detailing the difficulties faced in complying with customs control regulations with respect to cryptographic products, which were once classed as "munitions" by various jurisdictions including the United States.
Encrypted Media Extensions (EME) is a W3C specification for providing a communication channel between web browsers and the Content Decryption Module (CDM) software which implements digital rights management (DRM). This allows the use of HTML5 video to play back DRM-wrapped content such as streaming video services without the use of heavy third-party media plugins like Adobe Flash or Microsoft Silverlight. The use of a third-party key management system may be required, depending on whether the publisher chooses to scramble the keys.
FREAK is a security exploit of a cryptographic weakness in the SSL/TLS protocols introduced decades earlier for compliance with U.S. cryptography export regulations. These involved limiting exportable software to use only public key pairs with RSA moduli of 512 bits or fewer, with the intention of allowing them to be broken easily by the National Security Agency (NSA), but not by other organizations with lesser computing resources. However, by the early 2010s, increases in computing power meant that they could be broken by anyone with access to relatively modest computing resources using the well-known Number Field Sieve algorithm, using as little as $100 of cloud computing services. Combined with the ability of a man-in-the-middle attack to manipulate the initial cipher suite negotiation between the endpoints in the connection and the fact that the finished hash only depended on the master secret, this meant that a man-in-the-middle attack with only a modest amount of computation could break the security of any website that allowed the use of 512-bit export-grade keys. While the exploit was only discovered in 2015, its underlying vulnerabilities had been present for many years, dating back to the 1990s.
Logjam is a security vulnerability in systems that use Diffie–Hellman key exchange with the same prime number. It was discovered by a team of computer scientists and publicly reported on May 20, 2015. The discoverers were able to demonstrate their attack on 512-bit DH systems. They estimated that a state-level attacker could do so for 1024-bit systems, then widely used, thereby allowing decryption of a significant fraction of Internet traffic. They recommended upgrading to at least 2048 bits for shared prime systems.
Windows 10, a proprietary operating system released by Microsoft in July 2015, has been criticized by reviewers and users. Due to issues mostly about privacy, it has been the subject of a number of negative assessments by various groups.

BlueKeep is a security vulnerability that was discovered in Microsoft's Remote Desktop Protocol (RDP) implementation, which allows for the possibility of remote code execution.







