
Gen Digital Inc. is a multinational software company co-headquartered in Tempe, Arizona and Prague, Czech Republic. The company provides cybersecurity software and services. Gen is a Fortune 500 company and a member of the S&P 500 stock-market index. The company also has development centers in Pune, Chennai and Bangalore. Its portfolio includes Norton, Avast, LifeLock, Avira, AVG, ReputationDefender, and CCleaner.

Susan Ellen "Zoe" Lofgren is an American lawyer and politician serving as a U.S. representative from California. A member of the Democratic Party, Lofgren is in her 15th term in Congress, having been first elected in 1994. Lofgren has long served on the House Judiciary Committee, and chaired the House Administration Committee in the 116th and 117th Congresses.
L0phtCrack is a password auditing and recovery application originally produced by Mudge from L0pht Heavy Industries. It is used to test password strength and sometimes to recover lost Microsoft Windows passwords, by using dictionary, brute-force, hybrid attacks, and rainbow tables.

Kevin Lee Poulsen is an American former black-hat hacker and a contributing editor at The Daily Beast.
A grey hat is a computer hacker or computer security expert who may sometimes violate laws or typical ethical standards, but usually does not have the malicious intent typical of a black hat hacker.
Norton AntiVirus is an anti-virus or anti-malware software product founded by Peter Norton, developed and distributed by Symantec since 1990 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spam filtering and phishing protection.
Norton Internet Security, developed by Symantec Corporation, is a discontinued computer program that provides malware protection and removal during a subscription period. It uses signatures and heuristics to identify viruses. Other features include a personal firewall, email spam filtering, and phishing protection. With the release of the 2015 line in summer 2014, Symantec officially retired Norton Internet Security after 14 years as the chief Norton product. It was superseded by Norton Security, a rechristened adaptation of the original Norton 360 security suite. The suite was once again rebranded to Norton 360 in 2019.
Christien Rioux, also known by his handle DilDog, is the co-founder and chief scientist for the Burlington, Massachusetts based company Veracode, for which he is the main patent holder.

Peiter C. Zatko, better known as Mudge, is an American network security expert, open source programmer, writer, and hacker. He is currently the chief information officer of DARPA. He was the most prominent member of the high-profile hacker think tank the L0pht as well as the computer and culture hacking cooperative the Cult of the Dead Cow.

Chris Wysopal is an entrepreneur, computer security expert and co-founder and CTO of Veracode. He was a member of the high-profile hacker think tank the L0pht where he was a vulnerability researcher.

Cult of the Dead Cow, also known as cDc or cDc Communications, is a computer hacker and DIY media organization founded in 1984 in Lubbock, Texas. The group maintains a weblog on its site, also titled "[Cult of the Dead Cow]". New media are released first through the blog, which also features thoughts and opinions of the group's members.
Xcitium, formerly known as Comodo Security Solutions, Inc., is a cybersecurity company headquartered in Bloomfield, New Jersey. Under the brand Sectigo, the company acts as a web Certificate authority (CA) and issues SSL/TLS certificates.
ATstake, Inc. was a computer security professional services company in Cambridge, Massachusetts, United States. It was founded in 1999 by Battery Ventures and Ted Julian. Its initial core team of technologists included Dan Geer and the east coast security team from Cambridge Technology Partners. Its initial core team of executives included Christopher Darby, James T. Mobley, and Christina Luconi.
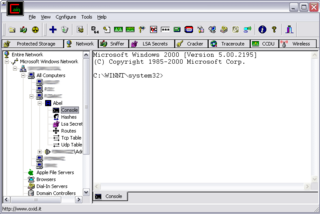
Cain and Abel was a password recovery tool for Microsoft Windows. It could recover many kinds of passwords using methods such as network packet sniffing, cracking various password hashes by using methods such as dictionary attacks, brute force and cryptanalysis attacks. Cryptanalysis attacks were done via rainbow tables which could be generated with the winrtgen.exe program provided with Cain and Abel. Cain and Abel was maintained by Massimiliano Montoro and Sean Babcock.
Rogue security software is a form of malicious software and internet fraud that misleads users into believing there is a virus on their computer and aims to convince them to pay for a fake malware removal tool that actually installs malware on their computer. It is a form of scareware that manipulates users through fear, and a form of ransomware. Rogue security software has been a serious security threat in desktop computing since 2008. An early example that gained infamy was SpySheriff and its clones, such as Nava Shield.

Joe Grand is an American electrical engineer, inventor and hardware hacker known in the hacker community as Kingpin. He achieved mainstream popularity after his appearance on Prototype This!, a Discovery Channel television show. He specializes in reverse engineering and finding security flaws in hardware devices. Grand has testified before the U.S. Senate Committee on Governmental Affairs regarding government and homeland computer security under his internet handle, Kingpin.
Michael Gregg is an American computer security specialist, businessman, author and co-author of several books, including Build Your Own Network Security Lab and Inside Network Security Assessment. He has also served as an expert witness before a congressional committee on cyber security and identity theft.
Browser security is the application of Internet security to web browsers in order to protect networked data and computer systems from breaches of privacy or malware. Security exploits of browsers often use JavaScript, sometimes with cross-site scripting (XSS) with a secondary payload using Adobe Flash. Security exploits can also take advantage of vulnerabilities that are commonly exploited in all browsers.

Cris Thomas is an American cybersecurity researcher, white hat hacker, and award winning best selling author. A founding member and researcher at the high-profile hacker security think tank L0pht Heavy Industries, Thomas was one of seven L0pht members who testified before the U.S. Senate Committee on Governmental Affairs (1998) on the topic of government and homeland computer security, specifically warning of internet vulnerabilities and claiming that the group could "take down the internet within 30 minutes".









