Solidity is an object-oriented programming language for writing smart contracts. It is used for implementing smart contracts on various blockchain platforms, most notably, Ethereum. It was developed by Gavin Wood, Christian Reitwiessner, Alex Beregszaszi, Liana Husikyan, Yoichi Hirai and several former Ethereum core contributors to enable writing smart contracts on blockchain platforms such as Ethereum.
The Sybil attack in computer security is an attack wherein a reputation system is subverted by forging identities in peer-to-peer networks. It is named after the subject of the book Sybil, a case study of a woman diagnosed with dissociative identity disorder. The name was suggested in or before 2002 by Brian Zill at Microsoft Research. The term pseudospoofing had previously been coined by L. Detweiler on the Cypherpunks mailing list and used in the literature on peer-to-peer systems for the same class of attacks prior to 2002, but this term did not gain as much influence as "Sybil attack".
Double-spending is a potential flaw in a digital cash scheme in which the same single digital token can be spent more than once. Unlike physical cash, a digital token consists of a digital file that can be duplicated or falsified. As with counterfeit money, such double-spending leads to inflation by creating a new amount of copied currency that did not previously exist. This devalues the currency relative to other monetary units or goods and diminishes user trust as well as the circulation and retention of the currency. Fundamental cryptographic techniques to prevent double-spending, while preserving anonymity in a transaction, are blind signatures and, particularly in offline systems, secret splitting.
Bitcoin (₿) is a cryptocurrency, a form of electronic cash. It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries.
The bitcoin network is a peer-to-peer payment network that operates on a cryptographic protocol. Users send and receive bitcoins, the units of currency, by broadcasting digitally signed messages to the network using bitcoin cryptocurrency wallet software. Transactions are recorded into a distributed, replicated public database known as the blockchain, with consensus achieved by a proof-of-work system called mining. Satoshi Nakamoto, the designer of bitcoin claimed that design and coding of bitcoin began in 2007. The project was released in 2009 as open source software.
A distributed ledger is a consensus of replicated, shared, and synchronized digital data geographically spread across multiple sites, countries, or institutions. There is no central administrator or centralized data storage.

Ethereum Classic is an open-source, public, blockchain-based distributed computing platform featuring smart contract (scripting) functionality. It provides a decentralized Turing-complete virtual machine, the Ethereum Virtual Machine (EVM), which can execute scripts using an international network of public nodes. Ethereum Classic and Ethereum have a value token called "ether", which can be transferred between participants, stored in a cryptocurrency wallet and is used to compensate participant nodes for computations performed in the Ethereum Platform. The classic ether token is traded on cryptocurrency exchanges under the ticker symbol ETC. Gas, an internal transaction pricing mechanism, is used to prevent spam on the network and allocate resources proportionally to the incentive offered by the request.
Vic Coin is a purely peer-to-peer version of digital currency that would allow online Settlements to be sent directly from one party to another without going through a Central counter party. Part of the solution lies with the digital signatures, but the main benefits are lost if a central counter party is still required to prevent public viewing. Vic Coin suggest a solution to the public-viewing problem using a peer-to-peer network. The system network time stamps all transactions by hashing Vic Coin into an ongoing chain of hash-based proof-of-work to form a record that cannot be changed without doing the proof-of-work all over again. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as master nodes that are not cooperating to attack the network control a majority of CPU power, Vic Coin will generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and master nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while Vic Coin were gone.
Bitcoin Unlimited (BU) is a full node implementation for the bitcoin and Bitcoin Cash networks. Compared to the Bitcoin Core client hard-coding the block size limit to one megabyte, from which it is forked, Bitcoin Unlimited allows users to signal which block size limit they prefer, find the limit having a majority consensus and automatically track the largest proof-of-work, regardless of block size. However, if a block greater than one megabyte in size is accepted by Bitcoin Unlimited and rejected by nodes with a block size limit, a fork of the network will occur, resulting in two separate blockchains with Bitcoin Unlimited nodes following the chain with the largest proof-of-work.
Dragonchain is a blockchain platform for enterprises. It was originally developed at The Walt Disney Company in Seattle in 2014 and then open-sourced in 2016. Despite extensive speculation, there is no current relationship between Disney and Dragonchain. The open source code is maintained by the Dragonchain Foundation. And the commercial blockchain platform is maintained by the commercial entity named Dragonchain, Inc. Dragonchain is a public/private hybrid blockchain platform. Developers can use existing smart contracts from the library or write their own smart contracts and build (decentralized) blockchain applications in known languages.

The bitcoin scalability problem refers to the discussion concerning the limits on the amount of transactions the bitcoin network can process. It is related to the fact that records in the bitcoin blockchain are limited in size and frequency.
Ethash is the proof-of-work function in Ethereum-based blockchain currencies. It uses Keccak, a hash function eventually standardized to SHA-3. These two are different, and should not be confused. Since version 1.0, Ethash has been designed to be ASIC-resistant via memory-hardness and easily verifiable. It also uses a slightly modified version of earlier Dagger and Hashimoto hashes to remove computational overhead. Previously referred to as Dagger-Hashimoto, the Ethash function has evolved over time. Ethash uses an initial 1 GB dataset known as the Ethash DAG and a 16 MB cache for light clients to hold. These are regenerated every 30,000 blocks, known as an epoch. Miners grab slices of the DAG to generate mix-hashes using transaction and receipt data, along with a cryptographic nonce to generate a hash below a dynamic target difficulty.

STEEM is a cryptocurrency based on the social media and content-focused Steem blockchain, which was created on March 24, 2016 by Ned Scott and the blockchain developer Dan Larimer. In terms of total market capitalization, STEEM is currently ranked at place 40. with a market capitalization of more than 159 million USD..
EOS.IO is a blockchain protocol powered by the native cryptocurrency EOS. The protocol emulates most of the attributes of a real computer including hardware with the computing resources distributed equally among EOS cryptocurrency holders. EOSIO operates as a smart contract platform and decentralized operating system intended for the deployment of industrial-scale decentralized applications through a decentralized autonomous corporation model. The smart contract platform claims to eliminate transaction fees and also conduct millions of transactions per second.
In blockchain, a fork is defined variously as:
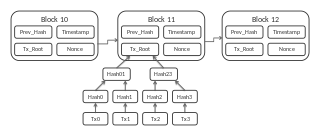
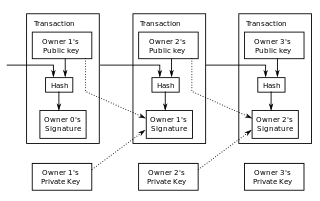
A blockchain is a public, shared database that records transactions between two parties. Blockchains document and confirm owners at a particular time through cryptography. After a transaction is validated and cryptographically verified by other participants or nodes in the network, it is made into a "block" on the blockchain. A block contains information about when the transaction occurred, previous transactions, and details about the transaction. Once recorded as a block, transactions are ordered chronologically and cannot be altered. This technology rose to popularity after the creation of Bitcoin—the first application built on using blockchain technology—and has catalyzed other cryptocurrencies and applications.
There are various different types of blockchain networks. Including but not limited to public, private and consortium blockchains. A hybrid blockchain solution is often used where multiple parties, trust, data access management and sharing, friction, regulations and a combination of centralization and decentralization is involved. A hybrid blockchain is also used by entities that need the benefits of both the public and private characteristics, which can be achieved using Interchain, bridges or other interoperability solutions between legacy systems and blockchains, both public or private.