Provable security refers to any type or level of security that can be proved. It is used in different ways by different fields.
Double-spending is a potential flaw in a digital cash scheme in which the same single digital token can be spent more than once. Unlike physical cash, a digital token consists of a digital file that can be duplicated or falsified. As with counterfeit money, such double-spending leads to inflation by creating a new amount of copied currency that did not previously exist. This devalues the currency relative to other monetary units or goods and diminishes user trust as well as the circulation and retention of the currency. Fundamental cryptographic techniques to prevent double-spending, while preserving anonymity in a transaction, are blind signatures and, particularly in offline systems, secret splitting.
Zerocoin is a privacy protocol proposed by Johns Hopkins University professor Matthew D. Green and his graduate students in 2013 as an extension to the Bitcoin protocol that would improve Bitcoin transactions' anonymity.
Proof of stake (PoS) is a type of algorithm by which a cryptocurrency blockchain network aims to achieve distributed consensus. In PoS-based cryptocurrencies the creator of the next block is chosen via various combinations of random selection and wealth or age. In contrast, the algorithm of proof-of-work-based cryptocurrencies such as bitcoin uses mining; that is, the solving of computationally intensive puzzles to validate transactions and create new blocks.
Ethereum is an open-source, public, blockchain-based distributed computing platform and operating system featuring smart contract (scripting) functionality. It supports a modified version of Nakamoto consensus via transaction-based state transitions.
Dash is an open source cryptocurrency and is a form of decentralized autonomous organization (DAO) run by a subset of users, called "masternodes". It is an altcoin that was forked from the Bitcoin protocol. The currency permits fast transactions that can be untraceable.
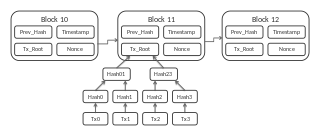
A blockchain, originally block chain, is a growing list of records, called blocks, which are linked using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data.
NEM is a peer-to-peer cryptocurrency and blockchain platform launched on March 29, 2015. Written in Java, with a C++ version in the works, NEM has a stated goal of a wide distribution model and has introduced new features to blockchain technology such as its proof-of-importance (POI) algorithm, multisignature accounts, encrypted messaging, and an Eigentrust++ reputation system. The NEM blockchain software is used in a commercial blockchain called Mijin, which is being tested by financial institutions and private companies in Japan and internationally.
Hyperledger is an umbrella project of open source blockchains and related tools, started in December 2015 by the Linux Foundation, and supported by big industry players like IBM, Intel and SAP Ariba, to support the collaborative development of blockchain-based distributed ledgers.
In computer security, proof of secure erasure (PoSE) or proof of erasure is a remote attestation protocol, by which an embedded device proves to a verifying party, that it has just erased (overwritten) all its writable memory. The purpose is to make sure that no malware remains in the device. After that typically a new software is installed into the device.

The Lightning Network is a "Layer 2" payment protocol that operates on top of a blockchain-based cryptocurrency. It enables fast transactions between participating nodes and has been touted as a solution to the Bitcoin scalability problem. It features a peer-to-peer system for making micropayments of cryptocurrency through a network of bidirectional payment channels without delegating custody of funds. Lightning Network implementation also simplifies atomic swaps.

The bitcoin scalability problem refers to the discussion concerning the limits on the amount of transactions the bitcoin network can process. It is related to the fact that records in the bitcoin blockchain are limited in size and frequency.
Ethash is the proof-of-work function in Ethereum-based blockchain currencies. It uses Keccak, a hash function eventually standardized to SHA-3. These two are different, and should not be confused. Since version 1.0, Ethash has been designed to be ASIC-resistant via memory-hardness and easily verifiable. It also uses a slightly modified version of earlier Dagger and Hashimoto hashes to remove computational overhead. Previously referred to as Dagger-Hashimoto, the Ethash function has evolved over time. Ethash uses an initial 1 GB dataset known as the Ethash DAG and a 16 MB cache for light clients to hold. These are regenerated every 30,000 blocks, known as an epoch. Miners grab slices of the DAG to generate mix-hashes using transaction and receipt data, along with a cryptographic nonce to generate a hash below a dynamic target difficulty.

STEEM is a cryptocurrency based on the social media and content-focused Steem blockchain, which was created on March 24, 2016 by Ned Scott and the blockchain developer Dan Larimer. With over 1.2 million registered accounts and a daily volume of more than a million signed operations, Steem is amongst the five blockchains with the highest level of activity. In terms of total market capitalization, STEEM is currently ranked at place 40. with a market capitalization of more than 159 million USD..
EOS.IO is a blockchain protocol powered by the native cryptocurrency EOS. The protocol emulates most of the attributes of a real computer including hardware with the computing resources distributed equally among EOS cryptocurrency holders. EOSIO operates as a smart contract platform and decentralized operating system intended for the deployment of industrial-scale decentralized applications through a decentralized autonomous corporation model. The smart contract platform claims to eliminate transaction fees and also conduct millions of transactions per second.
Proof-of-authority (PoA) is an algorithm used with blockchains that delivers comparatively fast transactions through a consensus mechanism based on identity as a stake.
Royal Mint Gold is a digital gold currency and a cryptocurrency backed by gold reserves in the UK Royal Mint. The Royal Mint began testing blockchain transactions in April 2017. The first test transaction was in August 2017. The rollout was originally scheduled to occur by the end of 2017. US-based CME Group is administering the trading. The Daily Telegraph said it "appears somewhat similar to an exchange-traded fund such as ETF Securities Physical Gold".
A blockchain is a public, shared database that records transactions between two parties. Specifically, blockchains document and confirm who owns what at a particular time through cryptography. After a particular transaction is validated and cryptographically verified by other participants, or nodes in the network, it is then made into a "block" on the blockchain. A block contains information about when the transaction occurred, previous transactions, and details about the transaction. Once recorded as a block, transactions are ordered chronologically and cannot be altered or changed. This technology rose to popularity after the creation of Bitcoin—the first application built on using blockchain technology—and has furthermore catalyzed other cryptocurrencies and applications. Due to its nature of decentralization, transactions and data are not verified and owned by one singular, overpowering entity as they are in typical systems. Rather, the validity of transactions are able to be confirmed by any node, or computer, that has access to the network. Additionally, blockchain technology secures and authenticates transactions and data through cryptography. With the rise and widespread adoption of technology, data breaches have become rampant and frequent. User information and data are often stored, mishandled, and misused, causing a threat to personal privacy. Currently, many are pushing for the widespread adoption of blockchain technology for its ability to increase user privacy, data protection, and data ownership.