Computer programming or coding is the composition of sequences of instructions, called programs, that computers can follow to perform tasks. It involves designing and implementing algorithms, step-by-step specifications of procedures, by writing code in one or more programming languages. Programmers typically use high-level programming languages that are more easily intelligible to humans than machine code, which is directly executed by the central processing unit. Proficient programming usually requires expertise in several different subjects, including knowledge of the application domain, details of programming languages and generic code libraries, specialized algorithms, and formal logic.

Grace Brewster Hopper was an American computer scientist, mathematician, and United States Navy rear admiral. She was a pioneer of computer programming. Hopper was the first to devise the theory of machine-independent programming languages, and used this theory to develop the FLOW-MATIC programming language and COBOL, an early high-level programming language still in use today. She was also one of the first programmers on the Harvard Mark I computer. She is credited with writing the first computer manual, "A Manual of Operation for the Automatic Sequence Controlled Calculator."

The DECSYSTEM-20 was a family of 36-bit Digital Equipment Corporation PDP-10 mainframe computers running the TOPS-20 operating system and was introduced in 1977.
In computing, a segmentation fault or access violation is a fault, or failure condition, raised by hardware with memory protection, notifying an operating system (OS) the software has attempted to access a restricted area of memory. On standard x86 computers, this is a form of general protection fault. The operating system kernel will, in response, usually perform some corrective action, generally passing the fault on to the offending process by sending the process a signal. Processes can in some cases install a custom signal handler, allowing them to recover on their own, but otherwise the OS default signal handler is used, generally causing abnormal termination of the process, and sometimes a core dump.
A software bug is a design defect (bug) in computer software. A computer program with many or serious bugs may be described as buggy.
An undocumented feature is an unintended or undocumented hardware operation, for example an undocumented instruction, or software feature found in computer hardware and software that is considered beneficial or useful. Sometimes the documentation is omitted through oversight, but undocumented features are sometimes not intended for use by end users, but left available for use by the vendor for software support and development. Also, some unintended operation of hardware or software that ends up being of utility to users is simply a bug, flaw or quirk.
RT-11 is a discontinued small, low-end, single-user real-time operating system for the full line of Digital Equipment Corporation PDP-11 16-bit computers. RT-11 was first implemented in 1970. It was widely used for real-time computing systems, process control, and data acquisition across all PDP-11s. It was also used for low-cost general-use computing.
Incompatible Timesharing System (ITS) is a time-sharing operating system developed principally by the MIT Artificial Intelligence Laboratory, with help from Project MAC. The name is the jocular complement of the MIT Compatible Time-Sharing System (CTSS).
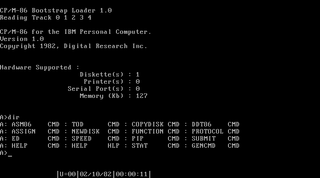
Dynamic Debugging Technique (DDT) is a series of debugger programs originally developed for Digital Equipment Corporation (DEC) hardware, initially known as DEC Debugging Tape because it was distributed on paper tape. The name is a pun on the insecticide DDT. The first version of DDT was developed at MIT for the PDP-1 computer in 1961, but newer versions on newer platforms continued to use the same name. After being ported to other vendor's platforms and changing media, the name was changed to the less DEC-centric version. Early versions of Digital Research's CP/M and CP/M-86 kept the DEC name DDT for their debugger, however, now meaning Dynamic Debugging Tool. The CP/M DDT was later superseded by the Symbolic Instruction Debugger in DR DOS and GEM.
A programming tool or software development tool is a computer program that is used to develop another program. A tool provides a command line interface (CLI), a graphical user interface (GUI), or both. A CLI allows a tool to be used for automation such as for build or test.
In systems engineering, dependability is a measure of a system's availability, reliability, maintainability, and in some cases, other characteristics such as durability, safety and security. In real-time computing, dependability is the ability to provide services that can be trusted within a time-period. The service guarantees must hold even when the system is subject to attacks or natural failures.

DECtape, originally called Microtape, is a magnetic tape data storage medium used with many Digital Equipment Corporation computers, including the PDP-6, PDP-8, LINC-8, PDP-9, PDP-10, PDP-11, PDP-12, and the PDP-15. On DEC's 32-bit systems, VAX/VMS support for it was implemented but did not become an official part of the product lineup.
The Harvard Mark II, also known as the Aiken Relay Calculator, was an electromechanical computer built under the direction of Howard Aiken at Harvard University, completed in 1947. It was financed by the United States Navy and used for ballistic calculations at Naval Proving Ground Dahlgren. Computer pioneers Edmund Berkeley and Grace Hopper worked together under Aiken to build and program the Mark II
In computer programming jargon, a heisenbug is a software bug that seems to disappear or alter its behavior when one attempts to study it. The term is a pun on the name of Werner Heisenberg, the physicist who first asserted the observer effect of quantum mechanics, which states that the act of observing a system inevitably alters its state. In electronics, the traditional term is probe effect, where attaching a test probe to a device changes its behavior.
A hardware bug is a bug in computer hardware. It is the hardware counterpart of software bug, a defect in software. A bug is different from a glitch which describes an undesirable behavior as more quick, transient and repeated than constant, and different from a quirk which is a behavior that may be considered useful even though not intentionally designed.

Windows Error Reporting (WER) is a crash reporting technology introduced by Microsoft with Windows XP and included in later Windows versions and Windows Mobile 5.0 and 6.0. Not to be confused with the Dr. Watson debugging tool which left the memory dump on the user's local machine, Windows Error Reporting collects and offers to send post-error debug information using the Internet to Microsoft when an application crashes or stops responding on a user's desktop. No data is sent without the user's consent. When a crash dump reaches the Microsoft server, it is analyzed, and information about a solution is sent back to the user if available. Solutions are served using Windows Error Reporting Responses. Windows Error Reporting runs as a Windows service. Kinshuman Kinshumann is the original architect of WER. WER was also included in the Association for Computing Machinery (ACM) hall of fame for its impact on the computing industry.
A metaphorical extension is the "extension of meaning in a new direction" through the popular adoption of an original metaphorical comparison.

In software, a feature is an identifiable characteristic of a computer program.
In engineering, debugging is the process of finding the root cause, workarounds and possible fixes for bugs.
The Jargon File is a glossary and usage dictionary of slang used by computer programmers. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab (SAIL) and others of the old ARPANET AI/LISP/PDP-10 communities, including Bolt, Beranek and Newman (BBN), Carnegie Mellon University, and Worcester Polytechnic Institute. It was published in paperback form in 1983 as The Hacker's Dictionary, revised in 1991 as The New Hacker's Dictionary.






