Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys to provide equivalent security, compared to cryptosystems based on modular exponentiation in Galois fields, such as the RSA cryptosystem and ElGamal cryptosystem.
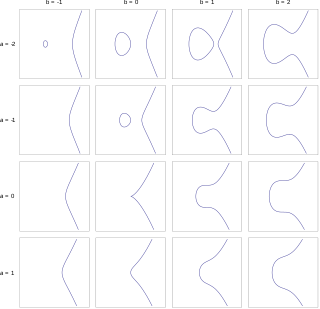
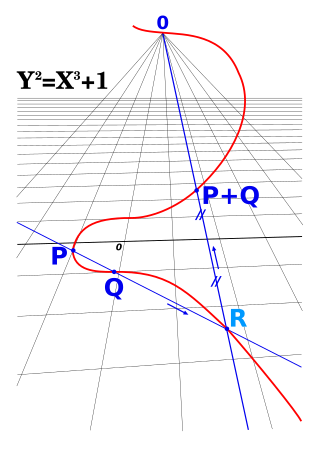
In mathematics, an elliptic curve is a smooth, projective, algebraic curve of genus one, on which there is a specified point O. An elliptic curve is defined over a field K and describes points in K2, the Cartesian product of K with itself. If the field's characteristic is different from 2 and 3, then the curve can be described as a plane algebraic curve which consists of solutions (x, y) for:
The Lenstra elliptic-curve factorization or the elliptic-curve factorization method (ECM) is a fast, sub-exponential running time, algorithm for integer factorization, which employs elliptic curves. For general-purpose factoring, ECM is the third-fastest known factoring method. The second-fastest is the multiple polynomial quadratic sieve, and the fastest is the general number field sieve. The Lenstra elliptic-curve factorization is named after Hendrik Lenstra.

In mathematics, particularly in algebraic geometry, complex analysis and algebraic number theory, an abelian variety is a projective algebraic variety that is also an algebraic group, i.e., has a group law that can be defined by regular functions. Abelian varieties are at the same time among the most studied objects in algebraic geometry and indispensable tools for research on other topics in algebraic geometry and number theory.
In algebraic geometry, a projective variety over an algebraically closed field k is a subset of some projective n-space over k that is the zero-locus of some finite family of homogeneous polynomials of n + 1 variables with coefficients in k, that generate a prime ideal, the defining ideal of the variety. Equivalently, an algebraic variety is projective if it can be embedded as a Zariski closed subvariety of .
In mathematics, restriction of scalars is a functor which, for any finite extension of fields L/k and any algebraic variety X over L, produces another variety ResL/kX, defined over k. It is useful for reducing questions about varieties over large fields to questions about more complicated varieties over smaller fields.

In algebraic geometry, a Kummer quartic surface, first studied by Ernst Kummer, is an irreducible nodal surface of degree 4 in with the maximal possible number of 16 double points. Any such surface is the Kummer variety of the Jacobian variety of a smooth hyperelliptic curve of genus 2; i.e. a quotient of the Jacobian by the Kummer involution x ↦ −x. The Kummer involution has 16 fixed points: the 16 2-torsion point of the Jacobian, and they are the 16 singular points of the quartic surface. Resolving the 16 double points of the quotient of a torus by the Kummer involution gives a K3 surface with 16 disjoint rational curves; these K3 surfaces are also sometimes called Kummer surfaces.
In mathematics, the canonical bundle of a non-singular algebraic variety of dimension over a field is the line bundle , which is the nth exterior power of the cotangent bundle on .
In mathematics, the Weil pairing is a pairing on the points of order dividing n of an elliptic curve E, taking values in nth roots of unity. More generally there is a similar Weil pairing between points of order n of an abelian variety and its dual. It was introduced by André Weil for Jacobians of curves, who gave an abstract algebraic definition; the corresponding results for elliptic functions were known, and can be expressed simply by use of the Weierstrass sigma function.
The decisional Diffie–Hellman (DDH) assumption is a computational hardness assumption about a certain problem involving discrete logarithms in cyclic groups. It is used as the basis to prove the security of many cryptographic protocols, most notably the ElGamal and Cramer–Shoup cryptosystems.
In computational number theory, the index calculus algorithm is a probabilistic algorithm for computing discrete logarithms. Dedicated to the discrete logarithm in where is a prime, index calculus leads to a family of algorithms adapted to finite fields and to some families of elliptic curves. The algorithm collects relations among the discrete logarithms of small primes, computes them by a linear algebra procedure and finally expresses the desired discrete logarithm with respect to the discrete logarithms of small primes.
In arithmetic geometry, the Mordell–Weil group is an abelian group associated to any abelian variety defined over a number field . It is an arithmetic invariant of the Abelian variety. It is simply the group of -points of , so is the Mordell–Weil grouppg 207. The main structure theorem about this group is the Mordell–Weil theorem which shows this group is in fact a finitely-generated abelian group. Moreover, there are many conjectures related to this group, such as the Birch and Swinnerton-Dyer conjecture which relates the rank of to the zero of the associated L-function at a special point.
In mathematics, the Abel–Jacobi map is a construction of algebraic geometry which relates an algebraic curve to its Jacobian variety. In Riemannian geometry, it is a more general construction mapping a manifold to its Jacobi torus. The name derives from the theorem of Abel and Jacobi that two effective divisors are linearly equivalent if and only if they are indistinguishable under the Abel–Jacobi map.
In 1998 Gerhard Frey firstly proposed using trace zero varieties for cryptographic purpose. These varieties are subgroups of the divisor class group on a low genus hyperelliptic curve defined over a finite field. These groups can be used to establish asymmetric cryptography using the discrete logarithm problem as cryptographic primitive.
A hyperelliptic curve is a particular kind of algebraic curve. There exist hyperelliptic curves of every genus . If the genus of a hyperelliptic curve equals 1, we simply call the curve an elliptic curve. Hence we can see hyperelliptic curves as generalizations of elliptic curves. There is a well-known group structure on the set of points lying on an elliptic curve over some field , which we can describe geometrically with chords and tangents. Generalizing this group structure to the hyperelliptic case is not straightforward. We cannot define the same group law on the set of points lying on a hyperelliptic curve, instead a group structure can be defined on the so-called Jacobian of a hyperelliptic curve. The computations differ depending on the number of points at infinity. Imaginary hyperelliptic curves are hyperelliptic curves with exactly 1 point at infinity: real hyperelliptic curves have two points at infinity.
An important aspect in the study of elliptic curves is devising effective ways of counting points on the curve. There have been several approaches to do so, and the algorithms devised have proved to be useful tools in the study of various fields such as number theory, and more recently in cryptography and Digital Signature Authentication. While in number theory they have important consequences in the solving of Diophantine equations, with respect to cryptography, they enable us to make effective use of the difficulty of the discrete logarithm problem (DLP) for the group , of elliptic curves over a finite field , where q = pk and p is a prime. The DLP, as it has come to be known, is a widely used approach to public key cryptography, and the difficulty in solving this problem determines the level of security of the cryptosystem. This article covers algorithms to count points on elliptic curves over fields of large characteristic, in particular p > 3. For curves over fields of small characteristic more efficient algorithms based on p-adic methods exist.
In mathematics the Function Field Sieve is one of the most efficient algorithms to solve the Discrete Logarithm Problem (DLP) in a finite field. It has heuristic subexponential complexity. Leonard Adleman developed it in 1994 and then elaborated it together with M. D. Huang in 1999. Previous work includes the work of D. Coppersmith about the DLP in fields of characteristic two.
In mathematics, there are two types of hyperelliptic curves, a class of algebraic curves: real hyperelliptic curves and imaginary hyperelliptic curves which differ by the number of points at infinity. Hyperelliptic curves exist for every genus . The general formula of Hyperelliptic curve over a finite field is given by
Network coding has been shown to optimally use bandwidth in a network, maximizing information flow but the scheme is very inherently vulnerable to pollution attacks by malicious nodes in the network. A node injecting garbage can quickly affect many receivers. The pollution of network packets spreads quickly since the output of honest node is corrupted if at least one of the incoming packets is corrupted.
This is a glossary of algebraic geometry.




















































