Related Research Articles
NESSIE was a European research project funded from 2000 to 2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Government-sponsored CRYPTREC project, but with notable differences from both. In particular, there is both overlap and disagreement between the selections and recommendations from NESSIE and CRYPTREC. The NESSIE participants include some of the foremost active cryptographers in the world, as does the CRYPTREC project.
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.
CRYPTREC is the Cryptography Research and Evaluation Committees set up by the Japanese Government to evaluate and recommend cryptographic techniques for government and industrial use. It is comparable in many respects to the European Union's NESSIE project and to the Advanced Encryption Standard process run by National Institute of Standards and Technology in the U.S.
In cryptography, MISTY1 is a block cipher designed in 1995 by Mitsuru Matsui and others for Mitsubishi Electric.
In cryptography, KHAZAD is a block cipher designed by Paulo S. L. M. Barreto together with Vincent Rijmen, one of the designers of the Advanced Encryption Standard (Rijndael). KHAZAD is named after Khazad-dûm, the fictional dwarven realm in the writings of J. R. R. Tolkien. KHAZAD was presented at the first NESSIE workshop in 2000, and, after some small changes, was selected as a finalist in the project.
In cryptography, SAFER is the name of a family of block ciphers designed primarily by James Massey on behalf of Cylink Corporation. Its first variant was published in 1993, and other variants were published until about 2000. The early SAFER K and SAFER SK designs share the same encryption function, but differ in the number of rounds and the key schedule. More recent versions – SAFER+ and SAFER++ – were submitted as candidates to the AES process in 1998 and the NESSIE project in 2000, respectively. All of the algorithms in the SAFER family are unpatented and available for unrestricted use.
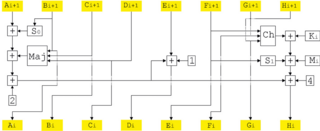
SHACAL-1 is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher based upon the larger hash function SHA-256.
NOEKEON is a family of two block ciphers designed by Joan Daemen, Michaël Peeters, Gilles Van Assche and Vincent Rijmen and submitted to the NESSIE project in September 2000. The two ciphers are "direct mode" NOEKEON, to be used for maximum efficiency where related-key attacks are not possible, and "indirect mode" NOEKEON where they are.
In cryptography, CS-Cipher is a block cipher invented by Jacques Stern and Serge Vaudenay in 1998. It was submitted to the NESSIE project, but was not selected.
eSTREAM is a project to "identify new stream ciphers suitable for widespread adoption", organised by the EU ECRYPT network. It was set up as a result of the failure of all six stream ciphers submitted to the NESSIE project. The call for primitives was first issued in November 2004. The project was completed in April 2008. The project was divided into separate phases and the project goal was to find algorithms suitable for different application profiles.
Anubis is a block cipher designed by Vincent Rijmen and Paulo S. L. M. Barreto as an entrant in the NESSIE project, a former research program initiated by the European Commission in 2000 for the identification of new cryptographic algorithms. Although the cipher has not been included in the final NESSIE portfolio, its design is considered very strong, and no attacks have been found by 2004 after the project had been concluded. The cipher is not patented and has been released by the designers for free public use.
SNOW is a family of word-based synchronous stream ciphers developed by Thomas Johansson and Patrik Ekdahl at Lund University.
Rabbit is a high-speed stream cipher from 2003. The algorithm and source code was released in 2008 as public domain software.
In cryptography, Nimbus is a block cipher invented by Alexis Machado in 2000. It was submitted to the NESSIE project, but was not selected.
In cryptography, Q is a block cipher invented by Leslie McBride. It was submitted to the NESSIE project, but was not selected.
In cryptography, SC2000 is a block cipher invented by a research group at Fujitsu Labs. It was submitted to the NESSIE project, but was not selected. It was among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, has been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, Grand Cru is a block cipher invented in 2000 by Johan Borst. It was submitted to the NESSIE project, but was not selected.
In cryptography, Hierocrypt-L1 and Hierocrypt-3 are block ciphers created by Toshiba in 2000. They were submitted to the NESSIE project, but were not selected. Both algorithms were among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, both have been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, SOBER is a family of stream ciphers initially designed by Greg Rose of QUALCOMM Australia starting in 1997. The name is a contrived acronym for Seventeen Octet Byte Enabled Register. Initially the cipher was intended as a replacement for broken ciphers in cellular telephony. The ciphers evolved, and other developers joined the project.
The following outline is provided as an overview of and topical guide to cryptography:
References
- ↑ "NESSIE submission for LILI-128" (zip). 2000-11-06. Retrieved 2018-09-13.
- ↑ Xiangao Huang; Wei Huang; Xiaozhou Liu; Chao Wang; Zhu jing Wang; Tao Wang (2007-02-22). "Reconstructing the Nonlinear Filter Function of LILI-128 Stream Cipher Based on Complexity". arXiv: cs/0702128 .