Related Research Articles

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
Bagle was a mass-mailing computer worm affecting Microsoft Windows. The first strain, Bagle.A, did not propagate widely. A second variant, Bagle.B, was considerably more virulent.

In computing, a zombie is a computer connected to the Internet that has been compromised by a hacker via a computer virus, computer worm, or trojan horse program and can be used to perform malicious tasks under the remote direction of the hacker. Zombie computers often coordinate together in a botnet controlled by the hacker, and are used for activities such as spreading e-mail spam and launching distributed denial-of-service attacks against web servers. Most victims are unaware that their computers have become zombies. The concept is similar to the zombie of Haitian Voodoo folklore, which refers to a corpse resurrected by a sorcerer via magic and enslaved to the sorcerer's commands, having no free will of its own. A coordinated DDoS attack by multiple botnet machines also resembles a "zombie horde attack", as depicted in fictional zombie films.

A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
Leonid Aleksandrovitch Kuvayev, who usually goes by the name of Leo, is a Russian/American spammer believed to be the ringleader of one of the world's biggest spam gangs. In 2005, he and six business partners were fined $37 million as a result of a lawsuit brought by the Massachusetts attorney general. It was found that they were responsible for millions of unsolicited e-mails per day. According to Spamhaus he could be the "Pharmamaster" spammer who performed a denial-of-service attack (DDoS) against the BlueSecurity company. Kuvayev is also behind countless phishing and money mule recruiting sites hosted on botnets. He has been called a "spam czar", and a "virtual criminal".

Bulletproof hosting (BPH) is technical infrastructure service provided by an Internet hosting service that is resilient to complaints of illicit activities, which serves criminal actors as a basic building block for streamlining various cyberattacks. BPH providers allow online gambling, illegal pornography, botnet command and control servers, spam, copyrighted materials, hate speech and misinformation, despite takedown court orders and law enforcement subpoenas, allowing such material in their acceptable use policies.

The Storm Worm is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:

The Storm botnet or Storm worm botnet was a remotely controlled network of "zombie" computers that had been linked by the Storm Worm, a Trojan horse spread through e-mail spam. At its height in September 2007, the Storm botnet was running on anywhere from 1 million to 50 million computer systems, and accounted for 8% of all malware on Microsoft Windows computers. It was first identified around January 2007, having been distributed by email with subjects such as "230 dead as storm batters Europe," giving it its well-known name. The botnet began to decline in late 2007, and by mid-2008 had been reduced to infecting about 85,000 computers, far less than it had infected a year earlier.
Srizbi BotNet is considered one of the world's largest botnets, and responsible for sending out more than half of all the spam being sent by all the major botnets combined. The botnets consist of computers infected by the Srizbi trojan, which sent spam on command. Srizbi suffered a massive setback in November 2008 when hosting provider Janka Cartel was taken down; global spam volumes reduced up to 93% as a result of this action.
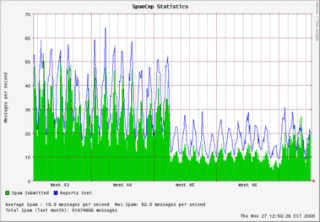
McColo was a US-based web hosting service provider that was, for a long time, the source of the majority of spam-sending activities for the entire world. In late 2008, the company was shut down by two upstream providers, Global Crossing and Hurricane Electric, because a significant amount of malware and botnets had been trafficking from the McColo servers.
The Rustock botnet was a botnet that operated from around 2006 until March 2011.
The Cutwail botnet, founded around 2007, is a botnet mostly involved in sending spam e-mails. The bot is typically installed on infected machines by a Trojan component called Pushdo. It affects computers running Microsoft Windows.
The Grum botnet, also known by its alias Tedroo and Reddyb, was a botnet mostly involved in sending pharmaceutical spam e-mails. Once the world's largest botnet, Grum can be traced back to as early as 2008. At the time of its shutdown in July 2012, Grum was reportedly the world's third largest botnet, responsible for 18% of worldwide spam traffic.
Waledac, also known by its aliases Waled and Waledpak, was a botnet mostly involved in e-mail spam and malware. In March 2010 the botnet was taken down by Microsoft.
The Lethic Botnet is a botnet consisting of an estimated 210 000 - 310 000 individual machines which are mainly involved in pharmaceutical and replica spam.
The Bredolab botnet, also known by its alias Oficla, was a Russian botnet mostly involved in viral e-mail spam. Before the botnet was eventually dismantled in November 2010 through the seizure of its command and control servers, it was estimated to consist of millions of zombie computers.

Oleg Yegorovich Nikolaenko is a Russian computer criminal who created the Mega-D botnet, violating the CAN-SPAM Act of 2003. Federal investigators believe his activities may have been responsible for as much as one third of the world's electronic spam.
The Kelihos botnet, also known as Hlux, is a botnet mainly involved in spamming and the theft of bitcoins.
Virut is a cybercrime malware botnet, operating at least since 2006, and one of the major botnets and malware distributors on the Internet. In January 2013 its operations were disrupted by the Polish organization Naukowa i Akademicka Sieć Komputerowa.

The Microsoft Digital Crimes Unit (DCU) is a Microsoft sponsored team of international legal and internet security experts employing the latest tools and technologies to stop or interfere with cyber crime and cyber threats. The Microsoft Digital Crimes Unit was assembled in 2008. In 2013, a Cybercrime center for the DCU was opened in Redmond, Washington. There are about 100 members of the DCU stationed just in Redmond, Washington at the original Cybercrime Center. Members of the DCU include lawyers, data scientists, investigators, forensic analysts, and engineers. The DCU has international offices located in major cities such as: Beijing, Berlin, Bogota, Delhi, Dublin, Hong Kong, Sydney, and Washington, D.C. The DCU's main focuses are child protection, copyright infringement and malware crimes. The DCU must work closely with law enforcement to ensure the perpetrators are punished to the full extent of the law. The DCU has taken down many major botnets such as the Citadel, Rustock, and Zeus. Around the world malware has cost users about $113 billion and the DCU's jobs is to shut them down in accordance with the law.
References
- ↑ "Storm worm dethroned by sex botnet". Networkworld.com. Archived from the original on 2012-04-02. Retrieved 2010-07-31.
- ↑ "New Mega-D botnet supersedes Storm". SPAMfighter. 2008-02-01. Retrieved 2010-07-31.
- ↑ "New Mega-D menace muscles Storm Worm aside". ars technica. February 2008. Retrieved 2011-12-06.
- ↑ Stone, Brad (October 14, 2008). "Authorities Shut Down Spam Ring". The New York Times.
- ↑ Smashing the Mega-d/Ozdok botnet in 24 hours
- ↑ Cheng, Jacqui (November 11, 2009). "Researchers' well-aimed stone takes down Goliath botnet". Ars Technica. Retrieved 2009-11-30.
- ↑ "Mega-D botnet takes a hit". M86 Security. November 9, 2009. Retrieved 2009-11-30.
- ↑ "Spam Statisti cs from the Security Labs team at M86 Security". M86 Security . Retrieved 2010-06-07.
- ↑ C.Y. Cho, D. Babic, R. Shin, and D. Song. Inference and Analysis of Formal Models of Botnet Command and Control Protocols, 2010 ACM Conference on Computer and Communications Security.
- ↑ Vielmetti, Bruce (December 3, 2010). "Milwaukee FBI agent trips up Russian 'king of spam'". Milwaukee Journal Sentinel . Retrieved December 3, 2010.
- ↑ Leyden, John (December 1, 2010). "Feds pursue Russian, 23, behind ⅓ of ALL WORLD SPAM". The Register . Retrieved December 3, 2010.