Proof of work (PoW) is a form of cryptographic proof in which one party proves to others that a certain amount of a specific computational effort has been expended. Verifiers can subsequently confirm this expenditure with minimal effort on their part. The concept was invented by Moni Naor and Cynthia Dwork in 1993 as a way to deter denial-of-service attacks and other service abuses such as spam on a network by requiring some work from a service requester, usually meaning processing time by a computer. The term "proof of work" was first coined and formalized in a 1999 paper by Markus Jakobsson and Ari Juels. The concept was adapted to digital tokens by Hal Finney in 2004 through the idea of "reusable proof of work" using the 160-bit secure hash algorithm 1 (SHA-1).
Ransomware is a type of cryptovirological malware that permanently blocks access to the victim's personal data unless a ransom is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem, and difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Double-spending is a monetary design problem, a good money is verifiably scarce and where a unit of value can be spent more than once, the monetary property of scarcity is challenged. As with counterfeit money, such double-spending leads to inflation by creating a new amount of copied currency that did not previously exist. Like all increasingly abundant resources, this devalues the currency relative to other monetary units or goods and diminishes user trust as well as the circulation and retention of the currency.

Bitcoin is the first decentralized cryptocurrency. Nodes in the peer-to-peer bitcoin network verify transactions through cryptography and record them in a public distributed ledger, called a blockchain, without central oversight. Consensus between nodes is achieved using a computationally intensive process based on proof of work, called mining, that guarantees the security of the bitcoin blockchain. Mining consumes increasing quantities of electricity and has been criticized for its environmental effects.

A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it.
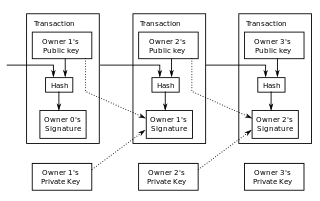
The Bitcoin protocol is the set of rules that govern the functioning of Bitcoin. Its key components and principles are: a peer-to-peer decentralized network with no central oversight; the blockchain technology, a public ledger that records all Bitcoin transactions; mining and proof of work, the process to create new bitcoins and verify transactions; and cryptographic security.
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running Microsoft Windows, and was believed to have first been posted to the Internet on 5 September 2013. It propagated via infected email attachments, and via an existing Gameover ZeuS botnet. When activated, the malware encrypted certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displayed a message which offered to decrypt the data if a payment was made by a stated deadline, and it threatened to delete the private key if the deadline passes. If the deadline was not met, the malware offered to decrypt data via an online service provided by the malware's operators, for a significantly higher price in bitcoin. There was no guarantee that payment would release the encrypted content.
A blockchain is a distributed ledger with growing lists of records (blocks) that are securely linked together via cryptographic hashes. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data. Since each block contains information about the previous block, they effectively form a chain, with each additional block linking to the ones before it. Consequently, blockchain transactions are irreversible in that, once they are recorded, the data in any given block cannot be altered retroactively without altering all subsequent blocks.

BTC-e was a cryptocurrency trading platform primarily serving the Russian market, with servers located in the United States. The U.S. government seized their website and funds in 2017. It was founded in July 2011 by Alexander Vinnik and Aleksandr Bilyuchenko, and as of February 2015 handled around 3% of all Bitcoin exchange volume. The platform was eventually taken over by Russian Orthodox oligarch Konstantin Malofeev, and funds from BTC-e were used for the war in Donbass, under the control of the FSB.
Monero is a cryptocurrency which uses a blockchain with privacy-enhancing technologies to obfuscate transactions to achieve anonymity and fungibility. Observers cannot decipher addresses trading Monero, transaction amounts, address balances, or transaction histories.
A cryptocurrency tumbler or cryptocurrency mixing service is a service that mixes potentially identifiable or "tainted" cryptocurrency funds with others, so as to obscure the trail back to the fund's original source. This is usually done by pooling together source funds from multiple inputs for a large and random period of time, and then spitting them back out to destination addresses. As all the funds are lumped together and then distributed at random times, it is very difficult to trace exact coins. Tumblers have arisen to improve the anonymity of cryptocurrencies, usually bitcoin, since the digital currencies provide a public ledger of all transactions. Due to its goal of anonymity, tumblers have been used to money launder cryptocurrency.
Lazarus Group is a hacker group made up of an unknown number of individuals, alleged to be run by the government of North Korea. While not much is known about the Lazarus Group, researchers have attributed many cyberattacks to them since 2010. Originally a criminal group, the group has now been designated as an advanced persistent threat due to intended nature, threat, and wide array of methods used when conducting an operation. Names given by cybersecurity organizations include Hidden Cobra and ZINC or Diamond Sleet. According to North Korean defector Kim Kuk-song, the unit is internally known in North Korea as 414 Liaison Office.

Locky is ransomware malware released in 2016. It is delivered by email with an attached Microsoft Word document that contains malicious macros. When the user opens the document, it appears to be full of gibberish, and includes the phrase "Enable macro if data encoding is incorrect," a social engineering technique. If the user does enable macros, they save and run a binary file that downloads the actual encryption Trojan, which will encrypt all files that match particular extensions. Filenames are converted to a unique 16 letter and number combination. Initially, only the .locky file extension was used for these encrypted files. Subsequently, other file extensions have been used, including .zepto, .odin, .aesir, .thor, and .zzzzz. After encryption, a message instructs them to download the Tor browser and visit a specific criminal-operated Web site for further information.
Cryptocurrency and crime describe notable examples of cybercrime related to theft of cryptocurrencies and some methods or security vulnerabilities commonly exploited. Cryptojacking is a form of cybercrime specific to cryptocurrencies that have been used on websites to hijack a victim's resources and use them for hashing and mining cryptocurrency.
The Zealot Campaign is a cryptocurrency mining malware collected from a series of stolen National Security Agency (NSA) exploits, released by the Shadow Brokers group on both Windows and Linux machines to mine cryptocurrency, specifically Monero. Discovered in December 2017, these exploits appeared in the Zealot suite include EternalBlue, EternalSynergy, and Apache Struts Jakarta Multipart Parser attack exploit, or CVE-2017-5638. The other notable exploit within the Zealot vulnerabilities includes vulnerability CVE-2017-9822, known as DotNetNuke (DNN) which exploits a content management system so that the user can install a Monero miner software. An estimated USD $8,500 of Monero having been mined on a single targeted computer. The campaign was discovered and studied extensively by F5 Networks in December 2017.
A blockchain is a shared database that records transactions between two parties in an immutable ledger. Blockchain documents and confirms pseudonymous ownership of all transactions in a verifiable and sustainable way. After a transaction is validated and cryptographically verified by other participants or nodes in the network, it is made into a "block" on the blockchain. A block contains information about the time the transaction occurred, previous transactions, and details about the transaction. Once recorded as a block, transactions are ordered chronologically and cannot be altered. This technology rose to popularity after the creation of Bitcoin, the first application of blockchain technology, which has since catalyzed other cryptocurrencies and applications.
Cryptojacking is the act of exploiting a computer to mine cryptocurrencies, often through websites, against the user's will or while the user is unaware. One notable piece of software used for cryptojacking was Coinhive, which was used in over two-thirds of cryptojacks before its March 2019 shutdown. The cryptocurrencies mined the most often are privacy coins—coins with hidden transaction histories—such as Monero and Zcash.
DarkSide is a cybercriminal hacking group, believed to be based in Russia, that targets victims using ransomware and extortion; it is believed to be behind the Colonial Pipeline cyberattack. It is thought that they have been able to hack and extort money from around 90 companies in the USA alone. The group provides ransomware as a service.
Exploit as a service (EaaS) is a scheme of cybercriminals whereby zero-day vulnerabilities are leased to hackers. EaaS is typically offered as a cloud service. By the end of 2021, EaaS became more of a trend among ransomware groups.
GPU mining is the use of Graphics Processing Units (GPUs) to "mine" proof-of-work cryptocurrencies, such as Bitcoin. Miners receive rewards for performing computationally intensive work, such as calculating hashes, that amend and verify transactions on an open and decentralized ledger. GPUs can be especially performant at calculating such hashes.




