
Identity theft occurs when someone uses another person's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term identity theft was coined in 1964. Since that time, the definition of identity theft has been statutorily defined throughout both the U.K. and the United States as the theft of personally identifiable information. Identity theft deliberately uses someone else's identity as a method to gain financial advantages or obtain credit and other benefits, and perhaps to cause other person's disadvantages or loss. The person whose identity has been stolen may suffer adverse consequences, especially if they are falsely held responsible for the perpetrator's actions. Personally identifiable information generally includes a person's name, date of birth, social security number, driver's license number, bank account or credit card numbers, PINs, electronic signatures, fingerprints, passwords, or any other information that can be used to access a person's financial resources.
Mobile payment generally refer to payment services operated under financial regulation and performed from or via a mobile device. Instead of paying with cash, cheque, or credit cards, a consumer can use a mobile to pay for a wide range of services and digital or hard goods. Although the concept of using non-coin-based currency systems has a long history, it is only in the 21st century that the technology to support such systems has become widely available.
Bank fraud is the use of potentially illegal means to obtain money, assets, or other property owned or held by a financial institution, or to obtain money from depositors by fraudulently posing as a bank or other financial institution. In many instances, bank fraud is a criminal offence. While the specific elements of particular banking fraud laws vary depending on jurisdictions, the term bank fraud applies to actions that employ a scheme or artifice, as opposed to bank robbery or theft. For this reason, bank fraud is sometimes considered a white-collar crime.
Phone fraud, or more generally communications fraud, is the use of telecommunications products or services with the intention of illegally acquiring money from, or failing to pay, a telecommunication company or its customers.

A prepaid mobile device is a mobile device such as a phone for which credit is purchased in advance of service use. The purchased credit is used to pay for telecommunications services at the point the service is accessed or consumed. If there is no credit, then access is denied by the cellular network/Intelligent Network. Users can top up their credit at any time using a variety of payment mechanisms.
An e-commerce payment system facilitates the acceptance of electronic payment for online transactions. Also known as a subcomponent of electronic data interchange (EDI), e-commerce payment systems have become increasingly popular due to the widespread use of the internet-based shopping and banking.
A chargeback is a return of money to a payer of some transaction, especially a credit card transaction.
Identity fraud is the use by one person of another person's personal information, without authorization, to commit a crime or to deceive or defraud that other person or a third person. Most identity fraud is committed in the context of financial advantages, such as accessing a victim's credit card, bank accounts, or loan accounts. False or forged identity documents have been used in criminal activity or in dealings with government agencies, such as immigration. Today, the identities of real persons are often used in the preparation of these false documents.
Telemarketing fraud is fraudulent selling conducted over the telephone. The term is also used for telephone fraud not involving selling.
An identity score is a system for detecting identity theft. Identity scores are increasingly being adopted as a means to prevent fraud in business and as a tool to verify and correct public records.
Internet fraud prevention is the act of stopping various types of internet fraud. Due to the many different ways of committing fraud over the Internet, such as stolen credit cards, identity theft, phishing, and chargebacks, users of the Internet, including online merchants, financial institutions and consumers who make online purchases, must make sure to avoid or minimize the risk of falling prey to such scams.

Sevici is a community bicycle program in Seville inaugurated in April 2007, modeled after the Vélo'v service in Lyon and Vélib' in Paris. Its purpose is to cover the small and medium daily routes within the city in a climate friendly way, almost without pollution, roadway noise, traffic congestion and to reclaim the urban streets with non-polluting vehicles.

Credit card fraud is an inclusive term for fraud committed using a payment card, such as a credit card or debit card. The purpose may be to obtain goods or services or to make payment to another account, which is controlled by a criminal. The Payment Card Industry Data Security Standard is the data security standard created to help financial institutions process card payments securely and reduce card fraud.
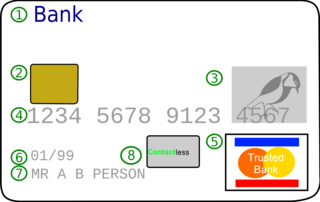
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt. The card issuer creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards, and a few gemstone-encrusted metal cards.
Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying information using wireless mechanics." Numerous articles have been written about wireless identity theft and broadcast television has produced several investigations of this phenomenon. According to Marc Rotenberg of the Electronic Privacy Information Center, wireless identity theft is a serious issue as the contactless (wireless) card design is inherently flawed, increasing the vulnerability to attacks.
Digital Security refers to various ways of protecting computer's internet account and files from intrusion by an outside user.

The 2011 PlayStation Network outage was the result of an "external intrusion" on Sony's PlayStation Network and Qriocity services, in which personal details from approximately 77 million accounts were compromised and prevented users of PlayStation 3 and PlayStation Portable consoles from accessing the service. The attack occurred between April 17 and April 19, 2011, forcing Sony to turn off the PlayStation Network on April 20. On May 4, Sony confirmed that personally identifiable information from each of the 77 million accounts had been exposed. The outage lasted 23 days.

Carding is a term describing the trafficking and unauthorized use of credit cards. The stolen credit cards or credit card numbers are then used to buy prepaid gift cards to cover up the tracks. Activities also encompass exploitation of personal data, and money laundering techniques. Modern carding sites have been described as full-service commercial entities.
SpyEye is a malware program that attacks users running Google Chrome, Opera, Firefox and Internet Explorer on Microsoft Windows operating systems. This malware uses keystroke logging and form grabbing to steal user credentials for malicious use. SpyEye allows hackers to steal money from online bank accounts and initiate transactions even while valid users are logged into their bank account.
Sinemia was a subscription-based service for discounted movie-ticket plans. Sinemia advertised a variety of subscription types, including those allowing users to watch movies in every format available at any movie theater with no limitation on the dates or movie showtimes, however the service was plagued with problems. Sinemia was the only international movie-ticket subscription service that operated in the UK, Canada, Turkey, and Australia alongside the US. Sinemia ceased operations in the US on April 26, 2019.






