
The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for applications, it has been highly influential in the advancement of cryptography.
In cryptography, 3-Way is a block cipher designed in 1994 by Joan Daemen. It is closely related to BaseKing; the two are variants of the same general cipher technique.
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.
In cryptography, KHAZAD is a block cipher designed by Paulo S. L. M. Barreto together with Vincent Rijmen, one of the designers of the Advanced Encryption Standard (Rijndael). KHAZAD is named after Khazad-dûm, the fictional dwarven realm in the writings of J. R. R. Tolkien. KHAZAD was presented at the first NESSIE workshop in 2000, and, after some small changes, was selected as a finalist in the project.
In cryptography, SHARK is a block cipher identified as one of the predecessors of Rijndael.

In cryptography, DES-X is a variant on the DES symmetric-key block cipher intended to increase the complexity of a brute-force attack using a technique called key whitening.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
In cryptography, LOKI89 and LOKI91 are symmetric-key block ciphers designed as possible replacements for the Data Encryption Standard (DES). The ciphers were developed based on a body of work analysing DES, and are very similar to DES in structure. The LOKI algorithms were named for Loki, the god of mischief in Norse mythology.

In cryptography, DEAL is a symmetric block cipher derived from the Data Encryption Standard (DES). The design was proposed in a report by Lars Knudsen in 1998, and was submitted to the AES contest by Richard Outerbridge.
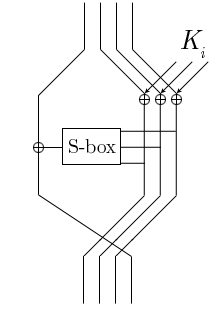
In cryptography, MacGuffin is a block cipher created in 1994 by Bruce Schneier and Matt Blaze at a Fast Software Encryption workshop. It was intended as a catalyst for analysis of a new cipher structure, known as Generalized Unbalanced Feistel Networks (GUFNs). The cryptanalysis proceeded very quickly, so quickly that the cipher was broken at the same workshop by Vincent Rijmen and Bart Preneel.

In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher.
In cryptography, impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences that propagate through the cipher with greater than expected probability, impossible differential cryptanalysis exploits differences that are impossible at some intermediate state of the cipher algorithm.
In cryptography, integral cryptanalysis is a cryptanalytic attack that is particularly applicable to block ciphers based on substitution–permutation networks. It was originally designed by Lars Knudsen as a dedicated attack against Square, so it is commonly known as the Square attack. It was also extended to a few other ciphers related to Square: CRYPTON, Rijndael, and SHARK. Stefan Lucks generalized the attack to what he called a saturation attack and used it to attack Twofish, which is not at all similar to Square, having a radically different Feistel network structure. Forms of integral cryptanalysis have since been applied to a variety of ciphers, including Hierocrypt, IDEA, Camellia, Skipjack, MISTY1, MISTY2, SAFER++, KHAZAD, and FOX.
In cryptography, BaseKing is a block cipher designed in 1994 by Joan Daemen. It is very closely related to 3-Way, as the two are variants of the same general cipher technique.
In cryptography, M6 is a block cipher proposed by Hitachi in 1997 for use in the IEEE 1394 FireWire standard. The design allows some freedom in choosing a few of the cipher's operations, so M6 is considered a family of ciphers.
In cryptography, KN-Cipher is a block cipher created by Kaisa Nyberg and Lars Knudsen in 1995. One of the first ciphers designed to be provably secure against ordinary differential cryptanalysis, KN-Cipher was later broken using higher order differential cryptanalysis.
In cryptography, truncated differential cryptanalysis is a generalization of differential cryptanalysis, an attack against block ciphers. Lars Knudsen developed the technique in 1994. Whereas ordinary differential cryptanalysis analyzes the full difference between two texts, the truncated variant considers differences that are only partially determined. That is, the attack makes predictions of only some of the bits instead of the full block. This technique has been applied to SAFER, IDEA, Skipjack, E2, Twofish, Camellia, CRYPTON, and even the stream cipher Salsa20.
In cryptography, M8 is a block cipher designed by Hitachi in 1999. The algorithm negotiates introduced in 1997 M6, with the modified key length, which is enlarged to 64 bits or more. This cipher operates with Feistel network and designed to reach high performance on small implementation or 32 bits devices. For instance, by using round numbers = 10 it present encryption speed at 32 Mbps for dedicated hardware of 6K gates and 25 MHz clock or 208 Mbps for program, that uses C-language and Pentium-I 266 MHz. Due to the openness of description, it should not be used in open or multivendor software.
In cryptography, decorrelation theory is a system developed by Serge Vaudenay in 1998 for designing block ciphers to be provably secure against differential cryptanalysis, linear cryptanalysis, and even undiscovered cryptanalytic attacks meeting certain broad criteria. Ciphers designed using these principles include COCONUT98 and the AES candidate DFC, both of which have been shown to be vulnerable to some forms of cryptanalysis not covered by the theory.
In cryptography, MultiSwap is a block cipher/MAC created by Microsoft in 1999 as part of its Windows Media DRM service (WMDRM). Microsoft's internal name for the algorithm is not publicly known; it was dubbed MultiSwap in a 2001 report on WMDRM under the pseudonym "Beale Screamer".




