Related Research Articles
In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks. They are specified elementary components in the design of many cryptographic protocols and are widely used to implement the encryption of large amounts of data, including data exchange protocols. It uses blocks as an unvarying transformation.

In cryptography, RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. The algorithm was one of the five finalists, and also was submitted to the NESSIE and CRYPTREC projects. It was a proprietary algorithm, patented by RSA Security.

In cryptography, CAST-128 is a symmetric-key block cipher used in a number of products, notably as the default cipher in some versions of GPG and PGP. It has also been approved for Government of Canada use by the Communications Security Establishment. The algorithm was created in 1996 by Carlisle Adams and Stafford Tavares using the CAST design procedure.
In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who did pioneering research while working for IBM (USA); it is also commonly known as a Feistel network. A large proportion of block ciphers use the scheme, including the US Data Encryption Standard, the Soviet/Russian GOST and the more recent Blowfish and Twofish ciphers. In a Feistel cipher, encryption and decryption are very similar operations, and both consist of iteratively running a function called a "round function" a fixed number of times.
In cryptography, Lucifer was the name given to several of the earliest civilian block ciphers, developed by Horst Feistel and his colleagues at IBM. Lucifer was a direct precursor to the Data Encryption Standard. One version, alternatively named DTD-1, saw commercial use in the 1970s for electronic banking.
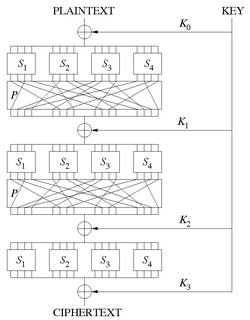
In cryptography, an SP-network, or substitution–permutation network (SPN), is a series of linked mathematical operations used in block cipher algorithms such as AES (Rijndael), 3-Way, Kalyna, Kuznyechik, PRESENT, SAFER, SHARK, and Square.
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.

In cryptography, LOKI97 is a block cipher which was a candidate in the Advanced Encryption Standard competition. It is a member of the LOKI family of ciphers, with earlier instances being LOKI89 and LOKI91. LOKI97 was designed by Lawrie Brown, assisted by Jennifer Seberry and Josef Pieprzyk.
In cryptography, MISTY1 is a block cipher designed in 1995 by Mitsuru Matsui and others for Mitsubishi Electric.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
In cryptography, SC2000 is a block cipher invented by a research group at Fujitsu Labs. It was submitted to the NESSIE project, but was not selected. It was among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, has been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, DFC is a symmetric block cipher which was created in 1998 by a group of researchers from École Normale Supérieure, CNRS, and France Télécom and submitted to the AES competition.
In cryptography, Hierocrypt-L1 and Hierocrypt-3 are block ciphers created by Toshiba in 2000. They were submitted to the NESSIE project, but were not selected. Both algorithms were among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, both have been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, E2 is a symmetric block cipher which was created in 1998 by NTT and submitted to the AES competition.
In cryptography, CIKS-1 is a block cipher designed in 2002 by A.A. Moldovyan and N.A. Moldovyan. Like its predecessor, Spectr-H64, it relies heavily on permutations of bits, so is better suited to implementation in hardware than in software.
In cryptography, CIPHERUNICORN-A is a block cipher created by NEC in 2000. It was among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003. However, it has been dropped to "candidate" level by the CRYPTREC revision of 2013.
In cryptography, COCONUT98 is a block cipher designed by Serge Vaudenay in 1998. It was one of the first concrete applications of Vaudenay's decorrelation theory, designed to be provably secure against differential cryptanalysis, linear cryptanalysis, and even certain types of undiscovered cryptanalytic attacks.
In cryptography, M8 is a block cipher designed by Hitachi in 1999. The algorithm negotiates introduced in 1997 M6, with the modified key length, which is enlarged to 64 bits or more. This cipher operates with Feistel network and designed to reach high performance on small implementation or 32 bits devices. For instance, by using round numbers = 10 it present encryption speed at 32 Mbit/s for dedicated hardware of 6K gates and 25 MHz clock or 208 Mbit/s for program, that uses C-language and Pentium-I 266 MHz. Due to the openness of description, it should not be used in open or multivendor software.
The BEAR and LION block ciphers were invented by Ross Anderson and Eli Biham by combining a stream cipher and a cryptographic hash function. The algorithms use a very large variable block size, on the order of 213 to 223 bits or more. Both are 3-round generalized (alternating) Feistel ciphers, using the hash function and the stream cipher as round functions. BEAR uses the hash function twice with independent keys, and the stream cipher once. LION uses the stream cipher twice and the hash function once. The inventors proved that an attack on either BEAR or LION that recovers the key would break both the stream cipher and the hash.
The following outline is provided as an overview of and topical guide to cryptography:
References
- ISO/IEC9979-0019 Register Entry (PDF), registered 6 July 1998 (includes sample implementation source code)
- Matt Robshaw (14 December 2001). "A Cryptographic Review of CIPHERUNICORN-E" (PDF). Retrieved 21 January 2007.Cite journal requires
|journal=(help) - David Wagner (17 December 2001). "An Evaluation of the Security of CIPHERUNICORN-E Against Certain Attacks" (PDF). Retrieved 21 January 2007.Cite journal requires
|journal=(help)