Related Research Articles
In cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building blocks of many cryptographic protocols. They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
In cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have been developed for block ciphers and stream ciphers. Linear cryptanalysis is one of the two most widely used attacks on block ciphers; the other being differential cryptanalysis.

Eli Biham is an Israeli cryptographer and cryptanalyst who is a professor at the Technion - Israel Institute of Technology Computer Science department. From 2008 to 2013, Biham was the dean of the Technion Computer Science department, after serving for two years as chief of CS graduate school. Biham invented (publicly) differential cryptanalysis, for which he received his Ph.D., while working under Adi Shamir. It had been invented before by a team at IBM during their Data Encryption Standard work; the National Security Agency told IBM to keep the discovery secret.
In cryptography, Lucifer was the name given to several of the earliest civilian block ciphers, developed by Horst Feistel and his colleagues at IBM. Lucifer was a direct precursor to the Data Encryption Standard. One version, alternatively named DTD-1, saw commercial use in the 1970s for electronic banking.
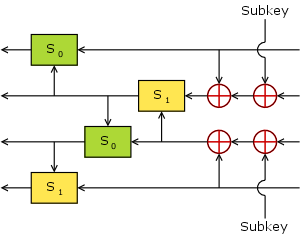
In cryptography, FEAL is a block cipher proposed as an alternative to the Data Encryption Standard (DES), and designed to be much faster in software. The Feistel based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT. The cipher is susceptible to various forms of cryptanalysis, and has acted as a catalyst in the discovery of differential and linear cryptanalysis.

In cryptography, LOKI97 is a block cipher which was a candidate in the Advanced Encryption Standard competition. It is a member of the LOKI family of ciphers, with earlier instances being LOKI89 and LOKI91. LOKI97 was designed by Lawrie Brown, assisted by Jennifer Seberry and Josef Pieprzyk.
In cryptography, CAST-256 is a symmetric-key block cipher published in June 1998. It was submitted as a candidate for the Advanced Encryption Standard (AES); however, it was not among the five AES finalists. It is an extension of an earlier cipher, CAST-128; both were designed according to the "CAST" design methodology invented by Carlisle Adams and Stafford Tavares. Howard Heys and Michael Wiener also contributed to the design.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
In cryptography, the eXtended Sparse Linearization (XSL) attack is a method of cryptanalysis for block ciphers. The attack was first published in 2002 by researchers Nicolas Courtois and Josef Pieprzyk. It has caused some controversy as it was claimed to have the potential to break the Advanced Encryption Standard (AES) cipher, also known as Rijndael, faster than an exhaustive search. Since AES is already widely used in commerce and government for the transmission of secret information, finding a technique that can shorten the amount of time it takes to retrieve the secret message without having the key could have wide implications.
In cryptography, REDOC II and REDOC III are block ciphers designed by cryptographer Michael Wood for Cryptech Inc and are optimised for use in software. Both REDOC ciphers are patented.

In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher.
Introduced by Martin Hellman and Susan K. Langford in 1994, the differential-linear attack is a mix of both linear cryptanalysis and differential cryptanalysis.
In cryptography, impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences that propagate through the cipher with greater than expected probability, impossible differential cryptanalysis exploits differences that are impossible at some intermediate state of the cipher algorithm.
In cryptography, integral cryptanalysis is a cryptanalytic attack that is particularly applicable to block ciphers based on substitution–permutation networks. It was originally designed by Lars Knudsen as a dedicated attack against Square, so it is commonly known as the Square attack. It was also extended to a few other ciphers related to Square: CRYPTON, Rijndael, and SHARK. Stefan Lucks generalized the attack to what he called a saturation attack and used it to attack Twofish, which is not at all similar to Square, having a radically different Feistel network structure. Forms of integral cryptanalysis have since been applied to a variety of ciphers, including Hierocrypt, IDEA, Camellia, Skipjack, MISTY1, MISTY2, SAFER++, KHAZAD, and FOX.
In cryptography, KN-Cipher is a block cipher created by Kaisa Nyberg and Lars Knudsen in 1995. One of the first ciphers designed to be provably secure against ordinary differential cryptanalysis, KN-Cipher was later broken using higher order differential cryptanalysis.
In cryptography, COCONUT98 is a block cipher designed by Serge Vaudenay in 1998. It was one of the first concrete applications of Vaudenay's decorrelation theory, designed to be provably secure against differential cryptanalysis, linear cryptanalysis, and even certain types of undiscovered cryptanalytic attacks.
In cryptography, truncated differential cryptanalysis is a generalization of differential cryptanalysis, an attack against block ciphers. Lars Knudsen developed the technique in 1994. Whereas ordinary differential cryptanalysis analyzes the full difference between two texts, the truncated variant considers differences that are only partially determined. That is, the attack makes predictions of only some of the bits instead of the full block. This technique has been applied to SAFER, IDEA, Skipjack, E2, Twofish, Camellia, CRYPTON, and even the stream cipher Salsa20.
In cryptography, the Davies attack is a dedicated statistical cryptanalysis method for attacking the Data Encryption Standard (DES). The attack was originally created in 1987 by Donald Davies. In 1994, Eli Biham and Alex Biryukov made significant improvements to the technique. It is a known-plaintext attack based on the non-uniform distribution of the outputs of pairs of adjacent S-boxes. It works by collecting many known plaintext/ciphertext pairs and calculating the empirical distribution of certain characteristics. Bits of the key can be deduced given sufficiently many known plaintexts, leaving the remaining bits to be found through brute force. There are tradeoffs between the number of required plaintexts, the number of key bits found, and the probability of success; the attack can find 24 bits of the key with 252 known plaintexts and 53% success rate.
In cryptography, partitioning cryptanalysis is a form of cryptanalysis for block ciphers. Developed by Carlo Harpes in 1995, the attack is a generalization of linear cryptanalysis. Harpes originally replaced the bit sums of linear cryptanalysis with more general balanced Boolean functions. He demonstrated a toy cipher that exhibits resistance against ordinary linear cryptanalysis but is susceptible to this sort of partitioning cryptanalysis. In its full generality, partitioning cryptanalysis works by dividing the sets of possible plaintexts and ciphertexts into efficiently-computable partitions such that the distribution of ciphertexts is significantly non-uniform when the plaintexts are chosen uniformly from a given block of the partition. Partitioning cryptanalysis has been shown to be more effective than linear cryptanalysis against variants of DES and CRYPTON. A specific partitioning attack called mod n cryptanalysis uses the congruence classes modulo some integer for partitions.
References
- Eli Biham, "New Types of Cryptanalytic Attacks Using Related Keys", Journal of Cryptology, vol 7 no 4, pp 229–246, Springer-Verlag, 1994.
- Eli Biham, Adi Shamir, "Differential Cryptanalysis of Snefru, Khafre, REDOC-II, LOKI and Lucifer", in Advances in Cryptology – CRYPTO'91, LNCS 576, pp 156–171, J Feigenbaum (ed), Springer-Verlag, 1991.
- L. Brown, Josef Pieprzyk and Jennifer Seberry, "LOKI - A Cryptographic Primitive for Authentication and Secrecy Applications", in Advances in Cryptology – Auscrypt'90, LNCS 453, pp229–236, J Seberry, J Pieprzyk (eds), Springer-Verlag, 1990.
- L. Brown, M Kwan, J Pieprzyk, J Seberry, " Improving Resistance to Differential Cryptanalysis and the Redesign of LOKI", in Advances in Cryptology – Asiacrypt'91", LNCs 739, pp 36–50, H Imai et al. (eds), Springer-Verlag, 1993.
- Lars R. Knudsen, "Cryptanalysis of LOKI", in Advances in Cryptology – ASIACRYPT'91, LNCS 739, pp 22–35, H Imai et al. (eds), Springer-Verlag, 1993.
- Lars R. Knudsen, "Cryptanalysis of LOKI91", in Advances in Cryptology – ASIACRYPT'92, LNCS 718, pp 196–208, J Seberry, Y Zheng (eds), Springer-Verlag, 1993.
- Lars R. Knudsen, "New Potentially 'Weak' Keys for DES and LOKI", in Advances in Cryptology – EUROCRYPT'94, LNCS 950, pp 419–424, Springer-Verlag, 1994.
- Lars R. Knudsen, M. J. B. Robshaw, "Non-linear Approximations in Linear Cryptanalysis", in Advances in Cryptology – Eurocrypt'96, LNCS 1070, pp 224–236, Springer-Verlag, 1996.
- Kouichi Sakurai, Souichi Furuya, "Improving Linear Cryptanalysis of LOKI91 by Probabilistic Counting Method", in Fast Software Encryption, pp 114–133, Springer-Verlag, 1997.
- Toshio Tokita, Tohru Sorimachi, Mitsuru Matsui, "Linear Cryptanalysis of LOKI and s2DES", in Advances in Cryptology – ASIACRYPT'94, LNCS 917, pp 293–303, Springer-Verlag, 1994.