Related Research Articles

The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
In cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building blocks of many cryptographic protocols. They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in information input can affect the resultant difference at the output. In the case of a block cipher, it refers to a set of techniques for tracing differences through the network of transformation, discovering where the cipher exhibits non-random behavior, and exploiting such properties to recover the secret key.

In cryptography, the International Data Encryption Algorithm (IDEA), originally called Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher designed by James Massey of ETH Zurich and Xuejia Lai and was first described in 1991. The algorithm was intended as a replacement for the Data Encryption Standard (DES). IDEA is a minor revision of an earlier cipher, the Proposed Encryption Standard (PES).
In cryptography, RC4 is a stream cipher. While it is remarkable for its simplicity and speed in software, multiple vulnerabilities have been discovered in RC4, rendering it insecure. It is especially vulnerable when the beginning of the output keystream is not discarded, or when nonrandom or related keys are used. Particularly problematic uses of RC4 have led to very insecure protocols such as WEP.
Articles related to cryptography include:

Eli Biham is an Israeli cryptographer and cryptanalyst who is a professor at the Technion - Israel Institute of Technology Computer Science department. From 2008 to 2013, Biham was the dean of the Technion Computer Science department, after serving for two years as chief of CS graduate school. Biham invented (publicly) differential cryptanalysis, for which he received his Ph.D., while working under Adi Shamir. It had been invented before by a team at IBM during their Data Encryption Standard work; the National Security Agency told IBM to keep the discovery secret.

The GOST block cipher (Magma), defined in the standard GOST 28147-89, is a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard, GOST R 34.12-2015, specifies that it may be referred to as Magma. The GOST hash function is based on this cipher. The new standard also specifies a new 128-bit block cipher called Kuznyechik.
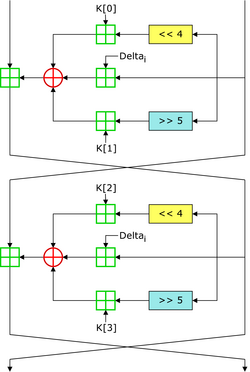
In cryptography, the Tiny Encryption Algorithm (TEA) is a block cipher notable for its simplicity of description and implementation, typically a few lines of code. It was designed by David Wheeler and Roger Needham of the Cambridge Computer Laboratory; it was first presented at the Fast Software Encryption workshop in Leuven in 1994, and first published in the proceedings of that workshop.
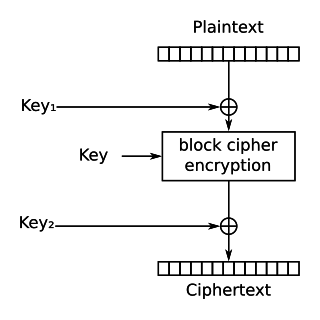
In cryptography, DES-X is a variant on the DES symmetric-key block cipher intended to increase the complexity of a brute-force attack. The technique used to increase the complexity is called key whitening.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.

In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher.
In cryptography, COCONUT98 is a block cipher designed by Serge Vaudenay in 1998. It was one of the first concrete applications of Vaudenay's decorrelation theory, designed to be provably secure against differential cryptanalysis, linear cryptanalysis, and even certain types of undiscovered cryptanalytic attacks.
In cryptography, rotational cryptanalysis is a generic cryptanalytic attack against algorithms that rely on three operations: modular addition, rotation and XOR — ARX for short. Algorithms relying on these operations are popular because they are relatively cheap in both hardware and software and run in constant time, making them safe from timing attacks in common implementations.
PRESENT is a lightweight block cipher, developed by the Orange Labs (France), Ruhr University Bochum (Germany) and the Technical University of Denmark in 2007. PRESENT was designed by Andrey Bogdanov, Lars R. Knudsen, Gregor Leander, Christof Paar, Axel Poschmann, Matthew J. B. Robshaw, Yannick Seurin, and C. Vikkelsoe. The algorithm is notable for its compact size.
A biclique attack is a variant of the meet-in-the-middle (MITM) method of cryptanalysis. It utilizes a biclique structure to extend the number of possibly attacked rounds by the MITM attack. Since biclique cryptanalysis is based on MITM attacks, it is applicable to both block ciphers and (iterated) hash-functions. Biclique attacks are known for having weakened both full AES and full IDEA, though only with slight advantage over brute force. It has also been applied to the KASUMI cipher and preimage resistance of the Skein-512 and SHA-2 hash functions.
Dmitry Khovratovich is a Russian cryptographer, currently a Lead Cryptographer for the Dusk Network, researcher for the Ethereum Foundation, and member of the International Association for Cryptologic Research.

Orr Dunkelman is an Israeli cryptographer and cryptanalyst, currently a professor at the University of Haifa Computer Science department. Dunkelman is a co-director of the Center for Cyber Law & Privacy at the University of Haifa and a co-founder of Privacy Israel, an Israeli NGO for promoting privacy in Israel.
In cryptography, a round or round function is a basic transformation that is repeated (iterated) multiple times inside the algorithm. Splitting a large algorithmic function into rounds simplifies both implementation and cryptanalysis.
References
- ↑ Vincent Rijmen (1997). "Cryptanalysis and Design of Iterated Block Ciphers". Ph.D. Thesis.
- ↑ Dahna McConnachie (2007-12-27). "Bruce Almighty: Schneier preaches security to Linux faithful". Computerworld. Archived from the original on 2012-06-03. Retrieved 2014-02-13.
- 1 2 Karthikeyan Bhargavan, Gaëtan Leurent (August 2016). "On the Practical (In-)Security of 64-bit Block Ciphers — Collision Attacks on HTTP over TLS and OpenVPN". ACM CCS 2016.
- ↑ Niels Ferguson (1999-10-05). "Impossible Differentials in Twofish". Schneier.
- ↑ Eli Biham; Orr Dunkelman; Nathan Keller (2002-02-04). Linear Cryptanalysis of Reduced Round Serpent. FSE 2002. doi: 10.1007/3-540-45473-X_2 .
- ↑ Junod, Pascal (2001). On the Complexity of Matsui's Attack. Selected Areas in Cryptography. pp. 199–211. Archived from the original on 2009-05-27.
- ↑ "DES Cracker Project". EFF. Archived from the original on May 7, 2017. Retrieved August 26, 2015.
On Wednesday, July 17, 1998 the EFF DES Cracker, which was built for less than $250,000, easily won RSA Laboratory's "DES Challenge II" contest and a $10,000 cash prize.
- ↑ "COPACOBANA – Special-Purpose Hardware for Code-Breaking".
- ↑ Stefan Lucks (1998-03-23). "Attacking Triple Encryption". Fast Software Encryption. Lecture Notes in Computer Science. Vol. 1372. Springer. pp. 239–253. doi: 10.1007/3-540-69710-1_16 . ISBN 978-3-540-64265-7.
- ↑ Orr Dunkelman; Nathan Keller; Adi Shamir (2010-01-10). "A Practical-Time Attack on the A5/3 Cryptosystem Used in Third Generation GSM Telephony". Cryptology ePrint Archive.
- ↑ Erik Tews; Ralf-Philipp Weinmann; Andrei Pyshkin (2007). Breaking 104 Bit WEP in Less Than 60 Seconds. WISA 2007.
- ↑ Scott Fluhrer; Itsik Mantin; Adi Shamir (2001-12-20). Weaknesses in the Key Scheduling Algorithm of RC4 (PDF). Selected Areas in Cryptography 2001.
- ↑ Scott R. Fluhrer; David A. McGrew. Statistical Analysis of the Alleged RC4 Keystream Generator (PDF). FSE 2000. pp. 19–30. Archived from the original (PDF) on 2014-05-02.
- 1 2 3 John Kelsey; Bruce Schneier; David Wagner (1997-11-11). "Related-key cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X NewDES, RC2, and TEA". In Yongfei Han; Tatsuaki Okamoto; Sihan Quing (eds.). Information and Communications Security: First International Conference. Vol. 1334. Springer. pp. 233–246. CiteSeerX 10.1.1.35.8112 . doi:10.1007/BFb0028479. ISBN 978-3-540-63696-0.
- ↑ Meiqin Wang; Xiaoyun Wang; Changhui Hu (2009-08-23). "New Linear Cryptanalytic Results of Reduced-Round of CAST-128 and CAST-256". Selected Areas in Cryptography. Lecture Notes in Computer Science. Vol. 5381. pp. 429–441. doi:10.1007/978-3-642-04159-4_28. ISBN 978-3-642-04158-7. S2CID 35612393.
- ↑ Achiya Bar-On (2015-07-30). "A 270 Attack on the Full MISTY1". Cryptology ePrint Archive.
- ↑ Yosuke Todo (2015-07-06). Integral Cryptanalysis on Full MISTY1. CRYPTO 2015.
- ↑ "ECRYPT II Yearly Report on Algorithms and Keysizes (2011-2012)" (PDF). CORDIS . 30 September 2012. D.SPA.20 Rev. 1.0, ICT-2007-216676 ECRYPT II.
- ↑ Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths, NIST
- ↑ Elias Yarrkov (2010-05-04). "Cryptanalysis of XXTEA". Cryptology ePrint Archive.
- ↑ Andrey Bogdanov; Gregor Leander; Kaisa Nyberg; Meiqin Wang (2012-12-04). "Integral and multidimensional linear distinguishers with correlation zero" (PDF). Advances in Cryptology – ASIACRYPT 2012: 18th International Conference on the Theory and Application of Cryptology and Information Security. Vol. 7658. Springer. pp. 244–261. doi:10.1007/978-3-642-34961-4. ISBN 978-3-642-34960-7. S2CID 26601027.