Related Research Articles
In cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building blocks of many cryptographic protocols. They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in information input can affect the resultant difference at the output. In the case of a block cipher, it refers to a set of techniques for tracing differences through the network of transformation, discovering where the cipher exhibits non-random behavior, and exploiting such properties to recover the secret key.
In cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have been developed for block ciphers and stream ciphers. Linear cryptanalysis is one of the two most widely used attacks on block ciphers; the other being differential cryptanalysis.
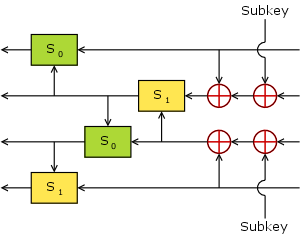
In cryptography, FEAL is a block cipher proposed as an alternative to the Data Encryption Standard (DES), and designed to be much faster in software. The Feistel based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT. The cipher is susceptible to various forms of cryptanalysis, and has acted as a catalyst in the discovery of differential and linear cryptanalysis.
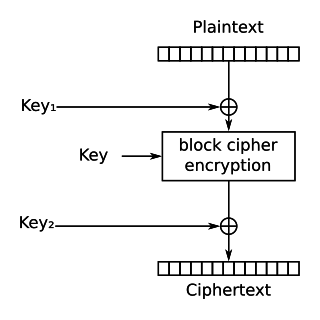
In cryptography, DES-X is a variant on the DES symmetric-key block cipher intended to increase the complexity of a brute-force attack. The technique used to increase the complexity is called key whitening.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
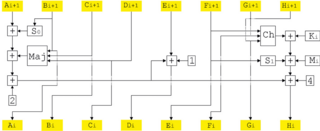
SHACAL-1 is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher based upon the larger hash function SHA-256.
In cryptography, REDOC II and REDOC III are block ciphers designed by Michael Wood (cryptographer) for Cryptech Inc and are optimised for use in software. Both REDOC ciphers are patented.
The slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number of rounds, which can ward off a differential attack. The slide attack works in such a way as to make the number of rounds in a cipher irrelevant. Rather than looking at the data-randomizing aspects of the block cipher, the slide attack works by analyzing the key schedule and exploiting weaknesses in it to break the cipher. The most common one is the keys repeating in a cyclic manner.

In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher.

Serge Vaudenay is a French cryptographer and professor, director of the Communications Systems Section at the École Polytechnique Fédérale de Lausanne
Introduced by Martin Hellman and Susan K. Langford in 1994, the differential-linear attack is a mix of both linear cryptanalysis and differential cryptanalysis.
In cryptography, DFC is a symmetric block cipher which was created in 1998 by a group of researchers from École Normale Supérieure, CNRS, and France Télécom and submitted to the AES competition.
In cryptography, KN-Cipher is a block cipher created by Kaisa Nyberg and Lars Knudsen in 1995. One of the first ciphers designed to be provably secure against ordinary differential cryptanalysis, KN-Cipher was later broken using higher order differential cryptanalysis.
In cryptography, the Davies attack is a dedicated statistical cryptanalysis method for attacking the Data Encryption Standard (DES). The attack was originally created in 1987 by Donald Davies. In 1994, Eli Biham and Alex Biryukov made significant improvements to the technique. It is a known-plaintext attack based on the non-uniform distribution of the outputs of pairs of adjacent S-boxes. It works by collecting many known plaintext/ciphertext pairs and calculating the empirical distribution of certain characteristics. Bits of the key can be deduced given sufficiently many known plaintexts, leaving the remaining bits to be found through brute force. There are tradeoffs between the number of required plaintexts, the number of key bits found, and the probability of success; the attack can find 24 bits of the key with 252 known plaintexts and 53% success rate.
In cryptography, decorrelation theory is a system developed by Serge Vaudenay in 1998 for designing block ciphers to be provably secure against differential cryptanalysis, linear cryptanalysis, and even undiscovered cryptanalytic attacks meeting certain broad criteria. Ciphers designed using these principles include COCONUT98 and the AES candidate DFC, both of which have been shown to be vulnerable to some forms of cryptanalysis not covered by the theory.
In cryptography, partitioning cryptanalysis is a form of cryptanalysis for block ciphers. Developed by Carlo Harpes in 1995, the attack is a generalization of linear cryptanalysis. Harpes originally replaced the bit sums of linear cryptanalysis with more general balanced Boolean functions. He demonstrated a toy cipher that exhibits resistance against ordinary linear cryptanalysis but is susceptible to this sort of partitioning cryptanalysis. In its full generality, partitioning cryptanalysis works by dividing the sets of possible plaintexts and ciphertexts into efficiently-computable partitions such that the distribution of ciphertexts is significantly non-uniform when the plaintexts are chosen uniformly from a given block of the partition. Partitioning cryptanalysis has been shown to be more effective than linear cryptanalysis against variants of DES and CRYPTON. A specific partitioning attack called mod n cryptanalysis uses the congruence classes modulo some integer for partitions.
This article summarizes publicly known attacks against block ciphers and stream ciphers. Note that there are perhaps attacks that are not publicly known, and not all entries may be up to date.

Orr Dunkelman is an Israeli cryptographer and cryptanalyst, currently a professor at the University of Haifa Computer Science department. Dunkelman is a co-director of the Center for Cyber Law & Privacy at the University of Haifa and a co-founder of Privacy Israel, an Israeli NGO for promoting privacy in Israel.
References
- 1 2 David Wagner (March 1999). The Boomerang Attack (PDF). 6th International Workshop on Fast Software Encryption (FSE '99). Rome: Springer-Verlag. pp. 156–170. doi:10.1007/3-540-48519-8_12 . Retrieved 7 October 2023.
- 1 2 Eli Biham, Orr Dunkelman, Nathan Keller (December 2002). Enhancing Differential-Linear Cryptanalysis (PDF/PostScript). Advances in Cryptology — Proceedings of ASIACRYPT 2002. Queenstown, New Zealand: Springer-Verlag. pp. 254–266. Retrieved 5 February 2007.
{{cite conference}}: CS1 maint: multiple names: authors list (link) - ↑ Serge Vaudenay (February 1998). Provable Security for Block Ciphers by Decorrelation. 15th Annual Symposium on Theoretical Aspects of Computer Science (STACS '98). Paris: Springer-Verlag. pp. 249–275. Archived from the original (PostScript) on 23 April 2007. Retrieved 26 February 2007.
- ↑ Serge Vaudenay (September 2003). "Decorrelation: A Theory for Block Cipher Security" (PDF). Journal of Cryptology . 16 (4): 249–286. doi:10.1007/s00145-003-0220-6. ISSN 0933-2790. S2CID 14252770. Archived from the original (PDF) on 21 February 2007. Retrieved 26 February 2007.
- ↑ Biham, Dunkelman, Keller (May 2005). Related-Key Boomerang and Rectangle Attacks (PostScript). Advances in Cryptology — Proceedings of EUROCRYPT 2005. Aarhus: Springer-Verlag. pp. 507–525. Retrieved 16 February 2007.
{{cite conference}}: CS1 maint: multiple names: authors list (link)[ permanent dead link ]