Related Research Articles
In general, a node is a localized swelling or a point of intersection.
Zigbee is an IEEE 802.15.4-based specification for a suite of high-level communication protocols used to create personal area networks with small, low-power digital radios, such as for home automation, medical device data collection, and other low-power low-bandwidth needs, designed for small scale projects which need wireless connection. Hence, Zigbee is a low-power, low data rate, and close proximity wireless ad hoc network.

A wireless mesh network (WMN) is a communications network made up of radio nodes organized in a mesh topology. It can also be a form of wireless ad hoc network.
Wireless sensor networks (WSNs) refer to networks of spatially dispersed and dedicated sensors that monitor and record the physical conditions of the environment and forward the collected data to a central location. WSNs can measure environmental conditions such as temperature, sound, pollution levels, humidity and wind.
In symmetric key cryptography, both parties must possess a secret key which they must exchange prior to using any encryption. Distribution of secret keys has been problematic until recently, because it involved face-to-face meeting, use of a trusted courier, or sending the key through an existing encryption channel. The first two are often impractical and always unsafe, while the third depends on the security of a previous key exchange.
A wireless ad hoc network (WANET) or mobile ad hoc network (MANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre-existing infrastructure, such as routers or wireless access points. Instead, each node participates in routing by forwarding data for other nodes. The determination of which nodes forward data is made dynamically on the basis of network connectivity and the routing algorithm in use.

Ian F. Akyildiz received his BS, MS, and PhD degrees in Electrical and Computer Engineering from the University of Erlangen-Nürnberg, Germany, in 1978, 1981 and 1984, respectively. Currently, he is the President and CTO of the Truva Inc. since March 1989. He retired from the School of Electrical and Computer Engineering (ECE) at Georgia Tech in 2021 after almost 35 years service as Ken Byers Chair Professor in Telecommunications and Chair of the Telecom group.

A sensor node, consists of an individual node from a sensor network that is capable of performing a desired action such as gathering, processing or communicating information with other connected nodes in a network.
Virgil Dorin Gligor is a Romanian-American professor of electrical and computer engineering who specializes in the research of network security and applied cryptography.

Underwater acoustic communication is a technique of sending and receiving messages in water. There are several ways of employing such communication but the most common is by using hydrophones. Underwater communication is difficult due to factors such as multi-path propagation, time variations of the channel, small available bandwidth and strong signal attenuation, especially over long ranges. Compared to terrestrial communication, underwater communication has low data rates because it uses acoustic waves instead of electromagnetic waves.
Routing in delay-tolerant networking concerns itself with the ability to transport, or route, data from a source to a destination, which is a fundamental ability all communication networks must have. Delay- and disruption-tolerant networks (DTNs) are characterized by their lack of connectivity, resulting in a lack of instantaneous end-to-end paths. In these challenging environments, popular ad hoc routing protocols such as AODV and DSR fail to establish routes. This is due to these protocols trying to first establish a complete route and then, after the route has been established, forward the actual data. However, when instantaneous end-to-end paths are difficult or impossible to establish, routing protocols must take to a "store and forward" approach, where data is incrementally moved and stored throughout the network in hopes that it will eventually reach its destination. A common technique used to maximize the probability of a message being successfully transferred is to replicate many copies of the message in hopes that one will succeed in reaching its destination.
A virtual sensor network (VSN) in computing and telecommunications is an emerging form of collaborative wireless sensor networks. In contrast to early wireless sensor networks that were dedicated to a specific application, VSNs enable multi-purpose, collaborative, and resource efficient WSNs. The key idea difference of VSNs is the collaboration and resource sharing. By doing so nodes achieve application objectives in a more resource efficient way. These networks may further involve dynamically varying subset of sensor nodes and/or users .
A VSN can be formed by providing logical connectivity among collaborative sensors. Nodes can be grouped into different VSNs based on the phenomenon they track or the task they perform. VSNs are expected to provide the protocol support for formation, usage, adaptation, and maintenance of subset of sensors collaborating on a specific task(s). Even the nodes that do not sense the particular event/phenomenon could be part of a VSN as far as they are willing to allow sensing nodes to communicate through them. Thus, VSNs make use of intermediate nodes, networks, or other VSNs to efficiently deliver messages across members of a VSN.
Topology control is a technique used in distributed computing to alter the underlying network to reduce the cost of distributed algorithms if run over the resulting graphs. It is a basic technique in distributed algorithms. For instance, a (minimum) spanning tree is used as a backbone to reduce the cost of broadcast from O(m) to O(n), where m and n are the number of edges and vertices in the graph, respectively.

PowWow is a wireless sensor network (WSN) mote developed by the Cairn team of IRISA/INRIA. The platform is currently based on IEEE 802.15.4 standard radio transceiver and on an MSP430 microprocessor. Unlike other available mote systems, PowWow offers specific features for a very-high energy efficiency:
A mobile wireless sensor network (MWSN) can simply be defined as a wireless sensor network (WSN) in which the sensor nodes are mobile. MWSNs are a smaller, emerging field of research in contrast to their well-established predecessor. MWSNs are much more versatile than static sensor networks as they can be deployed in any scenario and cope with rapid topology changes. However, many of their applications are similar, such as environment monitoring or surveillance. Commonly, the nodes consist of a radio transceiver and a microcontroller powered by a battery, as well as some kind of sensor for detecting light, heat, humidity, temperature, etc.
In mathematics and probability theory, continuum percolation theory is a branch of mathematics that extends discrete percolation theory to continuous space. More specifically, the underlying points of discrete percolation form types of lattices whereas the underlying points of continuum percolation are often randomly positioned in some continuous space and form a type of point process. For each point, a random shape is frequently placed on it and the shapes overlap each with other to form clumps or components. As in discrete percolation, a common research focus of continuum percolation is studying the conditions of occurrence for infinite or giant components. Other shared concepts and analysis techniques exist in these two types of percolation theory as well as the study of random graphs and random geometric graphs.
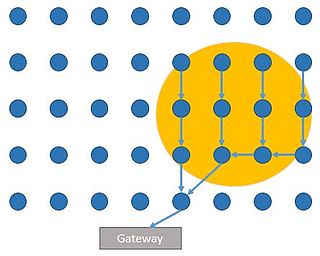
Wireless sensor networks (WSN) are a spatially distributed network of autonomous sensors used for monitoring an environment. Energy cost is a major limitation for WSN requiring the need for energy efficient networks and processing. One of major energy costs in WSN is the energy spent on communication between nodes and it is sometimes desirable to only send data to a gateway node when an event of interest is triggered at a sensor. Sensors will then only open communication during a probable event, saving on communication costs. Fields interested in this type of network include surveillance, home automation, disaster relief, traffic control, health care and more.
Time Slotted Channel Hopping or Time Synchronized Channel Hopping (TSCH) is a channel access method for shared-medium networks.
A Wireless Data center is a type of data center that uses wireless communication technology instead of cables to store, process and retrieve data for enterprises. The development of Wireless Data centers arose as a solution to growing cabling complexity and hotspots. The wireless technology was introduced by Shin et al., who replaced all cables with 60 GHz wireless connections at the Cayley data center.
In graph theory, LASCNN is a Localized Algorithm for Segregation of Critical/Non-critical Nodes The algorithm works on the principle of distinguishing between critical and non-critical nodes for network connectivity based on limited topology information. The algorithm finds the critical nodes with partial information within a few hops.
References
- ↑ "A Survey on Centralised and Distributed Clustering Routing Algorithms for WSNs". May 2015.
- ↑ Akyildiz, I.F., W. Su, Y. Sankarasubramaniam, and E. Cayirci, "A survey on sensor networks", IEEE Communications Magazine, vol.40, no.8, pp. 102-114, August 2002.
- ↑ Eschenauer, L. and V.D.Gligor, "A key management scheme for distributed sensor networks", in Proceedings of the 9th ACM conference on Computer and communications security, Washington DC, USA, November 18–22, 2002, 41-47.
- ↑ Blom, R.. An optimal class of symmetric key generation systems. Advances in Cryptology – Proceedings of EUROCRYPT 84 (Thomas Beth, Norbert Cot, and Ingemar Ingemarsson, eds.), Lecture Notes in Computer Science, Springer-Verlag, 209:335–338, 1985.
- ↑ Du, W. et al., A Pairwise Key Pre-distribution Scheme for Wireless Sensor Networks. ACM Transactions on Information and System Security, Vol. 8, No. 2, May 2005, Pages 228–258 http://www.cis.syr.edu/~wedu/Research/paper/ccs10_sensor.pdf