The underlying mathematics
Anonymous internet banking depends on the mathematics of public key cryptography and blind signature algorithms. In this simple example we have Alice and Bob and a banker. The banker generates an RSA public key with modulus  , where
, where  and
and  are large primes, making
are large primes, making  a semiprime. As described in RSA operation, the bank also generates public key exponent
a semiprime. As described in RSA operation, the bank also generates public key exponent  and private key exponent
and private key exponent  .
.

In cryptography a blind signature, as introduced by David Chaum, is a form of digital signature in which the content of a message is disguised (blinded) before it is signed. The resulting blind signature can be publicly verified against the original, unblinded message in the manner of a regular digital signature. Blind signatures are typically employed in privacy-related protocols where the signer and message author are different parties. Examples include cryptographic election systems and digital cash schemes.
Alice and Bob are fictional characters commonly used as placeholder names in cryptology, as well as science and engineering literature. The Alice and Bob characters were invented by Ron Rivest, Adi Shamir, and Leonard Adleman in their 1978 paper "A method for obtaining digital signatures and public-key cryptosystems." Subsequently, they have become common archetypes in many scientific and engineering fields, such as quantum cryptography, game theory and physics. As the use of Alice and Bob became more popular, additional characters were added, each with a particular meaning. These characters do not have to refer to humans, they refer to generic agents which might be different computers or even different programs running on a single computer.
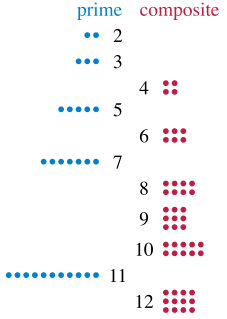
A prime number is a natural number greater than 1 that cannot be formed by multiplying two smaller natural numbers. A natural number greater than 1 that is not prime is called a composite number. For example, 5 is prime because the only ways of writing it as a product, 1 × 5 or 5 × 1, involve 5 itself. However, 6 is composite because it is the product of two numbers that are both smaller than 6. Primes are central in number theory because of the fundamental theorem of arithmetic: every natural number greater than 1 is either a prime itself or can be factorized as a product of primes that is unique up to their order.
Bob asks the banker for a $100 deposit slip in anticipation of Alice wanting to transfer money to him. To generate a deposit slip the bank selects a large, globally unique random number  and encrypts it using the bank's public key; this means that it can only be decrypted with the bank's secret key:
and encrypts it using the bank's public key; this means that it can only be decrypted with the bank's secret key:

A deposit slip is a form supplied by a bank for a depositor to fill out, designed to document in categories the items included in the deposit transaction. The categories include type of item, and if it is a cheque, where it is from such as a local bank or a state if the bank is not local. The teller keeps the deposit slip along with the deposit, and provides the depositor with a receipt. They are filled in a store and not a bank, so it is very convenient in paying. They also are a means of transport of money. Pay-in slips encourage the sorting of cash and coins, are filled in and signed by the person who deposited the money, and some tear off from a record that is also filled in by the depositor. Deposit slips are also called deposit tickets and come in a variety of designs. They are signed by the depositor if the depositor is cashing some of the accompanying check and depositing the rest.

A random number generator (RNG) is a device that generates a sequence of numbers or symbols that cannot be reasonably predicted better than by a random chance. Random number generators can be true hardware random-number generators (HRNG), which generate genuinely random numbers, or pseudo-random number generators (PRNG) which generate numbers which look random, but are actually deterministic, and can be reproduced if the state of the PRNG is known.

This encrypted value  is sent to Bob with the promise to deposit $100 into his account when Bob sends the value
is sent to Bob with the promise to deposit $100 into his account when Bob sends the value  back to the bank. The bank is confident that Bob won't be able to break RSA to generate
back to the bank. The bank is confident that Bob won't be able to break RSA to generate  from
from  within a reasonable period without knowledge of
within a reasonable period without knowledge of  , so it does not worry about handing out the deposit slips without receiving anything from Bob.
, so it does not worry about handing out the deposit slips without receiving anything from Bob.
When Alice wants to pay Bob $100 she asks for the deposit slip and Bob sends her  . Alice selects a large random value
. Alice selects a large random value  coprime with
coprime with  (so as to have an inverse modulo
(so as to have an inverse modulo  ) and uses it to blind
) and uses it to blind  and sends it to the bank to be blind signed. The Bank charges Alice $100 for this operation and returns the blind signed value
and sends it to the bank to be blind signed. The Bank charges Alice $100 for this operation and returns the blind signed value  . Due to the symmetric properties of RSA, this provides her with
. Due to the symmetric properties of RSA, this provides her with  :
:

Because of the blinding process, the Bank is not able to associate  or
or  with
with  or
or  . The only possible way for the bank to do this is to trial divide
. The only possible way for the bank to do this is to trial divide  by all the values of
by all the values of  that it gave out or
that it gave out or  by all values of
by all values of  . This means the bank is unable to determine that Bob and Alice are doing business together, preserving the anonymity of the transaction. Alice unblinds
. This means the bank is unable to determine that Bob and Alice are doing business together, preserving the anonymity of the transaction. Alice unblinds  (by dividing it by
(by dividing it by  ) to generate the original value
) to generate the original value  , which she sends to Bob. Bob verifies that
, which she sends to Bob. Bob verifies that  can be encrypted with the bank's public key by computing
can be encrypted with the bank's public key by computing  , which means that Alice has deposited $100 into the bank. Bob then sends this value to the bank and the bank checks its records to be sure that
, which means that Alice has deposited $100 into the bank. Bob then sends this value to the bank and the bank checks its records to be sure that  has not been already used. If
has not been already used. If  is confirmed to be unused the bank then deposits $100 into Bob's account and updates its database that the unique value
is confirmed to be unused the bank then deposits $100 into Bob's account and updates its database that the unique value  has been redeemed.
has been redeemed.
Different public keys can be used for different denominations of currency so this system doesn't take appreciably longer for large transactions.
Note that if neither Alice nor Bob wishes the bank to know that they performed a transaction with each other, then it is hard for the bank to find out. However, in order to ensure this is the case many people need to be making transactions at the same time. Otherwise the bank can figure it out by the timing of the transactions, using traffic analysis.
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication, which can be performed even when the messages are encrypted. In general, the greater the number of messages observed, or even intercepted and stored, the more can be inferred from the traffic. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is a concern in computer security.
This page is based on this
Wikipedia article Text is available under the
CC BY-SA 4.0 license; additional terms may apply.
Images, videos and audio are available under their respective licenses.



















