
John Marlan Poindexter is a retired United States naval officer and Department of Defense official. He was Deputy National Security Advisor and National Security Advisor during the Reagan administration. He was convicted in April 1990 of multiple felonies as a result of his actions in the Iran–Contra affair, but his convictions were reversed on appeal in 1991. During the George W. Bush administration, he served a brief stint as the director of the DARPA Information Awareness Office. He is the father of NASA astronaut and U.S. Navy Captain Alan G. Poindexter.

Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing, or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.

Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Combat Zones That See, or CTS, is a project of the United States Defense Advanced Research Projects Agency (DARPA) whose goal is to "track everything that moves" in a city by linking up a massive network of surveillance cameras to a centralized computer system. Artificial intelligence software will then identify and track all vehicle movement throughout the city.
The Policy Analysis Market (PAM), part of the FutureMAP project, was a proposed futures exchange developed, beginning in May 2001, by the Information Awareness Office (IAO) of the United States Defense Advanced Research Projects Agency (DARPA), and based on an idea first proposed by Net Exchange, a San Diego, California, research firm specializing in the development of online prediction markets. PAM was shut down in August 2003 after multiple US senators condemned it as an assassination and terrorism market, a characterization criticized in turn by futures-exchange expert Robin Hanson of George Mason University, and several journalists. Since PAM's closure, several private-sector variations on the idea have been launched.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is often distinguished from targeted surveillance.
The Multistate Anti-Terrorism Information Exchange Program, also known by the acronym MATRIX, was a U.S. federally funded data mining system originally developed for the Florida Department of Law Enforcement described as a tool to identify terrorist subjects.
Policy appliances are technical control and logging mechanisms to enforce or reconcile policy rules and to ensure accountability in information systems. Policy appliances can be used to enforce policy or other systems constraints within and among trusted systems.
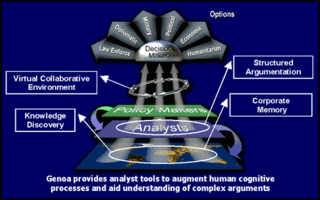
Project Genoa was a software project commissioned by the United States' DARPA which was designed to analyze large amounts of data and metadata to help human analysts counter terrorism.
Counterintelligence Field Activity (CIFA) was a United States Department of Defense (DoD) agency whose size and budget were classified. The CIFA was created by a directive from the Secretary of Defense, then Donald Rumsfeld, on February 19, 2002. On August 8, 2008, it was announced that CIFA would be shut down. The Defense Intelligence Agency (DIA) absorbed most of the components and authorities of the CIFA into the Defense Counterintelligence and Human Intelligence Center, which was later consolidated into the Defense Clandestine Service.
ADVISE is a research and development program within the United States Department of Homeland Security (DHS) Threat and Vulnerability Testing and Assessment (TVTA) portfolio. It is reportedly developing a massive data mining system, which would collect and analyze data on everyone in the United States and perform a "threat analysis" on them. The data can be anything from financial records, phone records, emails, blog entries, website searches, to any other electronic information that can be put into a computer system. This information is then analyzed, and used to monitor social threats such as community-forming, terrorism, political organizing, or crime.

The Disruptive Technology Office (DTO) was a funding agency within the United States Intelligence Community. It was previously known as the Advanced Research and Development Activity (ARDA). In December 2007, DTO was folded into the newly created IARPA.
K. A. (Kim) Taipale is a Finnish-American investor and legal scholar specializing in information, technology, and national security policy. He is a partner in Stilwell Holding, a private investment firm, a director of the Stilwell Charitable Fund, and the former chairman of the executive committee of Kobra International Ltd.
Investigative Data Warehouse (IDW) is a searchable database operated by the FBI. It was created in 2004. Much of the nature and scope of the database is classified. The database is a centralization of multiple federal and state databases, including criminal records from various law enforcement agencies, the U.S. Department of the Treasury's Financial Crimes Enforcement Network (FinCEN), and public records databases. According to Michael Morehart's testimony before the House Committee on Financial Services in 2006, the "IDW is a centralized, web-enabled, closed system repository for intelligence and investigative data. This system, maintained by the FBI, allows appropriately trained and authorized personnel throughout the country to query for information of relevance to investigative and intelligence matters."
Saffron Technology, Inc., was a technology company headquartered in Cary, North Carolina, that developed cognitive computing systems. Their systems use incremental learning to understand and unify by entity the connections between an entity and other “things” in data, along with the context of their connections and their raw frequency counts. Saffron learns from all sources of data including structured and unstructured data to support knowledge-based decision making. Its patented technology captures the connections between data points at the entity level and stores these connections in an associative memory. Similarity algorithms and predictive analytics are then combined with the associative index to identify patterns in the data. Saffron’s Natural Intelligence platform was utilized across industries including manufacturing, energy, defense and healthcare, to help decision-makers manage risks, identify opportunities and anticipate future outcomes, thus reducing cost and increasing productivity. Its competitors include IBM Watson and Grok. Intel purchased the company in 2015, then shuttered it less than 3 years later.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

The Watchers: The Rise of America's Surveillance State is a non-fiction book by American journalist Shane Harris, published in 2010. It details the rise of surveillance programs in the U.S. Author Harris had previously served as a writer for outfits such as Foreign Policy, National Journal, and The Washingtonian.

Project Genoa II was a software project that originated with the United States Defense Advanced Research Projects Agency's Information Awareness Office and the successor to the Genoa program. Originally part of DARPA's wider Total Information Awareness project, it was later renamed Topsail and handed over to the Advanced Research and Development Activity for further development.














