In the Internet, a domain name is a string that identifies a realm of administrative autonomy, authority or control. Domain names are often used to identify services provided through the Internet, such as websites, email services and more. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name identifies a network domain or an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, or a server computer.

Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim navigates the site, and transverses any additional security boundaries with the victim. As of 2020, it is the most common type of cybercrime, with the FBI's Internet Crime Complaint Center reporting more incidents of phishing than any other type of cybercrime.
Internet security is a branch of computer security. It encompasses the Internet, browser security, web site security, and network security as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet. The Internet is an inherently insecure channel for information exchange, with high risk of intrusion or fraud, such as phishing, online viruses, trojans, ransomware and worms.
Email fraud is intentional deception for either personal gain or to damage another individual using email as the vehicle. Almost as soon as email became widely used, it began to be used as a means to defraud people, just as telephony and paper mail were used by previous generations.
DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver's cache, causing the name server to return an incorrect result record, e.g. an IP address. This results in traffic being diverted to any computer that the attacker chooses.
Pharming is a cyberattack intended to redirect a website's traffic to another, fake site by installing a malicious program on the victim's computer in order to gain access to it. Pharming can be conducted either by changing the hosts file on a victim's computer or by exploitation of a vulnerability in DNS server software. DNS servers are computers responsible for resolving Internet names into their real IP addresses. Compromised DNS servers are sometimes referred to as "poisoned". Pharming requires unprotected access to target a computer, such as altering a customer's home computer, rather than a corporate business server.
The internationalized domain name (IDN) homoglyph attack is a method used by malicious parties to deceive computer users about what remote system they are communicating with, by exploiting the fact that many different characters look alike. For example, the Cyrillic, Greek and Latin alphabets each have a letter ⟨o⟩ that has the same shape but represents different sounds or phonemes in their respective writing systems.
Crimeware is a class of malware designed specifically to automate cybercrime.
Email spoofing is the creation of email messages with a forged sender address. The term applies to email purporting to be from an address which is not actually the sender's; mail sent in reply to that address may bounce or be delivered to an unrelated party whose identity has been faked. Disposable email address or "masked" email is a different topic, providing a masked email address that is not the user's normal address, which is not disclosed, but forwards mail sent to it to the user's real address.
PaypaI is a phishing scam, which targets account holders of the widely used internet payment service, PayPal, taking advantage of the fact that a capital "i" may be difficult to distinguish from a lower-case "L" in some computer fonts. This is a form of a homograph attack.
Voice phishing, or vishing, is the use of telephony to conduct phishing attacks.
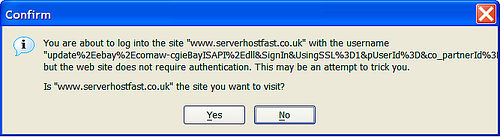
Website spoofing is the act of creating a website with the intention of misleading readers that the website has been created by a different person or organization.
Internet fraud prevention is the act of stopping various types of internet fraud. Due to the many different ways of committing fraud over the Internet, such as stolen credit cards, identity theft, phishing, and chargebacks, users of the Internet, including online merchants, financial institutions and consumers who make online purchases, must make sure to avoid or minimize the risk of falling prey to such scams.

Credit card fraud is an inclusive term for fraud committed using a payment card, such as a credit card or debit card. The purpose may be to obtain goods or services or to make payment to another account, which is controlled by a criminal. The Payment Card Industry Data Security Standard is the data security standard created to help financial institutions process card payments securely and reduce card fraud.

In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements, except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked until an additional step is performed.
Typosquatting, also called URL hijacking, a sting site, a cousin domain, or a fake URL, is a form of cybersquatting, and possibly brandjacking which relies on mistakes such as typos made by Internet users when inputting a website address into a web browser. A user accidentally entering an incorrect website address may be led to any URL, including an alternative website owned by a cybersquatter.
SmartScreen is a cloud-based anti-phishing and anti-malware component included in several Microsoft products:
Trojan.Win32.DNSChanger is a backdoor trojan that redirects users to various malicious websites through the means of altering the DNS settings of a victim's computer. The malware strain was first discovered by Microsoft Malware Protection Center on December 7, 2006 and later detected by McAfee Labs on April 19, 2009.
Internet security awareness or Cyber security awareness refers to how much end-users know about the cyber security threats their networks face, the risks they introduce and mitigating security best practices to guide their behavior. End users are considered the weakest link and the primary vulnerability within a network. Since end-users are a major vulnerability, technical means to improve security are not enough. Organizations could also seek to reduce the risk of the human element. This could be accomplished by providing security best practice guidance for end users' awareness of cyber security. Employees could be taught about common threats and how to avoid or mitigate them.