Related Research Articles

Internet Explorer is a retired series of graphical web browsers developed by Microsoft that were used in the Windows line of operating systems. While IE has been discontinued on most Windows editions, it remains supported on certain editions of Windows, such as Windows 10 LTSB/LTSC. Starting in 1995, it was first released as part of the add-on package Plus! for Windows 95 that year. Later versions were available as free downloads or in-service packs and included in the original equipment manufacturer (OEM) service releases of Windows 95 and later versions of Windows. Microsoft spent over US$100 million per year on Internet Explorer in the late 1990s, with over 1,000 people involved in the project by 1999. New feature development for the browser was discontinued in 2016 and ended support on June 15, 2022 for Windows 10 Semi-Annual Channel (SAC), in favor of its successor, Microsoft Edge.
Windows 9x is a generic term referring to a series of Microsoft Windows computer operating systems produced from 1995 to 2000, which were based on the Windows 95 kernel and its underlying foundation of MS-DOS, both of which were updated in subsequent versions. The first version in the 9x series was Windows 95, which was succeeded by Windows 98 and then Windows Me, which was the third and last version of Windows on the 9x line, until the series was superseded by Windows XP.
The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
In computer security, mandatory access control (MAC) refers to a type of access control by which a secured environment constrains the ability of a subject or initiator to access or modify on an object or target. In the case of operating systems, the subject is a process or thread, while objects are files, directories, TCP/UDP ports, shared memory segments, or IO devices. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, the operating system kernel examines these security attributes, examines the authorization rules in place, and decides whether to grant access. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects are tables, views, procedures, etc.
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager, and user interfaces can all use the registry. The registry also allows access to counters for profiling system performance.
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software vulnerabilities from spreading. The sandbox metaphor derives from the concept of a child's sandbox—a play area where kids can build, destroy, and experiment without causing any real-world damage. It is often used to execute untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. A sandbox typically provides a tightly controlled set of resources for guest programs to run in, such as storage and memory scratch space. Network access, the ability to inspect the host system, or read from input devices are usually disallowed or heavily restricted.

Windows Internet Explorer 7 (IE7) is a version of Internet Explorer, a web browser for Windows. It was released by Microsoft on October 18, 2006. It was the first major update to the browser since 2001. It does not support earlier versions of Windows.
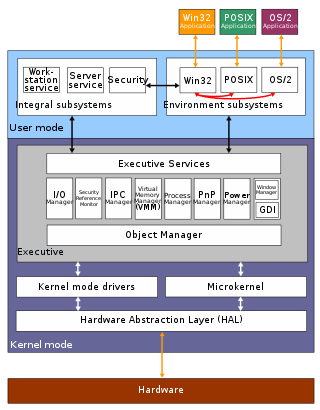
The architecture of Windows NT, a line of operating systems produced and sold by Microsoft, is a layered design that consists of two main components, user mode and kernel mode. It is a preemptive, reentrant multitasking operating system, which has been designed to work with uniprocessor and symmetrical multiprocessor (SMP)-based computers. To process input/output (I/O) requests, it uses packet-driven I/O, which utilizes I/O request packets (IRPs) and asynchronous I/O. Starting with Windows XP, Microsoft began making 64-bit versions of Windows available; before this, there were only 32-bit versions of these operating systems.
ntoskrnl.exe, also known as the kernel image, contains the kernel and executive layers of the Microsoft Windows NT kernel, and is responsible for hardware abstraction, process handling, and memory management. In addition to the kernel and executive layers, it contains the cache manager, security reference monitor, memory manager, scheduler (Dispatcher), and blue screen of death.

BitLocker is a full volume encryption feature included with Microsoft Windows versions starting with Windows Vista. It is designed to protect data by providing encryption for entire volumes. By default, it uses the Advanced Encryption Standard (AES) algorithm in cipher block chaining (CBC) or "xor–encrypt–xor (XEX)-based Tweaked codebook mode with ciphertext Stealing" (XTS) mode with a 128-bit or 256-bit key. CBC is not used over the whole disk; it is applied to each individual sector.

User Account Control (UAC) is a mandatory access control enforcement feature introduced with Microsoft's Windows Vista and Windows Server 2008 operating systems, with a more relaxed version also present in Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows 8.1, Windows Server 2012 R2, Windows 10, and Windows 11. It aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an administrator authorises an increase or elevation. In this way, only applications trusted by the user may receive administrative privileges and malware are kept from compromising the operating system. In other words, a user account may have administrator privileges assigned to it, but applications that the user runs do not inherit those privileges unless they are approved beforehand or the user explicitly authorises it.
In computing, a shatter attack is a programming technique employed by hackers on Microsoft Windows operating systems to bypass security restrictions between processes in a session. A shatter attack takes advantage of a design flaw in Windows's message-passing system whereby arbitrary code could be injected into any other running application or service in the same session, that makes use of a message loop. This could result in a privilege escalation exploit.
In the context of the Microsoft Windows NT line of operating systems, a Security Identifier (SID) is a unique, immutable identifier of a user, user group, or other security principal. A security principal has a single SID for life, and all properties of the principal, including its name, are associated with the SID. This design allows a principal to be renamed without affecting the security attributes of objects that refer to the principal.
Windows Display Driver Model is the graphic driver architecture for video card drivers running Microsoft Windows versions beginning with Windows Vista.
There are a number of security and safety features new to Windows Vista, most of which are not available in any prior Microsoft Windows operating system release.
Windows Vista has many significant new features compared with previous Microsoft Windows versions, covering most aspects of the operating system.
User Interface Privilege Isolation (UIPI) is a technology introduced in Windows Vista and Windows Server 2008 to combat shatter attack exploits. By making use of Mandatory Integrity Control, it prevents processes with a lower "integrity level" (IL) from sending messages to higher IL processes.
Security descriptors are data structures of security information for securable Windows objects, that is objects that can be identified by a unique name. Security descriptors can be associated with any named objects, including files, folders, shares, registry keys, processes, threads, named pipes, services, job objects and other resources.
Windows XP and Windows Vista differ considerably in regards to their security architecture, networking technologies, management and administration, shell and user interface, and mobile computing. Windows XP has suffered criticism for security problems and issues with performance. Vista has received criticism for issues with performance and product activation. Another common criticism of Vista concerns the integration of new forms of DRM into the operating system, and User Account Control (UAC) security technology.
Browser security is the application of Internet security to web browsers in order to protect networked data and computer systems from breaches of privacy or malware. Security exploits of browsers often use JavaScript, sometimes with cross-site scripting (XSS) with a secondary payload using Adobe Flash. Security exploits can also take advantage of vulnerabilities that are commonly exploited in all browsers.
References
- 1 2 3 Matthew Conover. "Analysis of the Windows Vista Security Model" (PDF). Symantec Corporation. Archived from the original (PDF) on 2008-05-16. Retrieved 2007-10-08.
- 1 2 Riley, Steve (22 July 2006). "Mandatory Integrity Control in Windows Vista". Microsoft Docs Archive. Microsoft.
- 1 2 3 Russinovich, Mark (12 February 2007). "PsExec, User Account Control and Security Boundaries". Windows Blog Archive. Microsoft.
- ↑ "CreateRemoteThread function". Windows Dev Center. Microsoft. 5 December 2018.
- ↑ "WriteProcessMemory function". Windows Dev Center. Microsoft. 5 December 2018.
- ↑ Brad Arkin (2010-07-10). "Introducing Adobe Reader Protected Mode". Adobe Systems . Retrieved 2010-09-10.
- ↑ "Plan Protected View settings for Office 2010". Microsoft Docs Archive. Microsoft. 5 August 2011.
- ↑ Keizer, Gregg (August 19, 2009). "Microsoft struts Office 2010 'sandbox' security". Computerworld . IDG . Retrieved January 23, 2017.