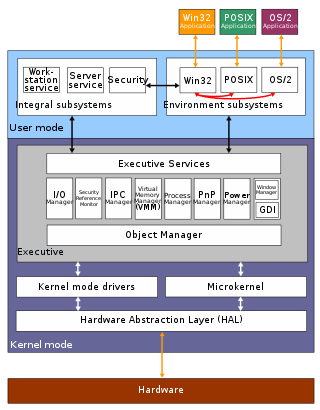
The Graphics Device Interface (GDI) is a legacy component of Microsoft Windows responsible for representing graphical objects and transmitting them to output devices such as monitors and printers. It was superseded by DirectDraw API and later Direct2D API. Windows apps use Windows API to interact with GDI, for such tasks as drawing lines and curves, rendering fonts, and handling palettes. The Windows USER subsystem uses GDI to render such UI elements as window frames and menus. Other systems have components that are similar to GDI; for example: Mac OS has QuickDraw, and Linux and Unix have X Window System core protocol.
Windows Management Instrumentation (WMI) consists of a set of extensions to the Windows Driver Model that provides an operating system interface through which instrumented components provide information and notification. WMI is Microsoft's implementation of the Web-Based Enterprise Management (WBEM) and Common Information Model (CIM) standards from the Distributed Management Task Force (DMTF).

Single sign-on (SSO) is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, software systems.
Identity management (IdM), also known as identity and access management, is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. IdM systems fall under the overarching umbrellas of IT security and data management. Identity and access management systems not only identify, authenticate, and control access for individuals who will be utilizing IT resources but also the hardware and applications employees need to access.

The Liberty Alliance Project was an organization formed in September 2001 to establish standards, guidelines and best practices for identity management in computer systems. It grew to more than 150 organizations, including technology vendors, consumer-facing companies, educational organizations and governments. It released frameworks for federation, identity assurance, an Identity Governance Framework, and Identity Web Services.

A one-time password (OTP), also known as a one-time PIN, one-time passcode, one-time authorization code (OTAC) or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid several shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to something a person has as well as something a person knows.
A federated identity in information technology is the means of linking a person's electronic identity and attributes, stored across multiple distinct identity management systems.

OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites using a third-party identity provider (IDP) service, eliminating the need for webmasters to provide their own ad hoc login systems, and allowing users to log in to multiple unrelated websites without having to have a separate identity and password for each. Users create accounts by selecting an OpenID identity provider, and then use those accounts to sign on to any website that accepts OpenID authentication. Several large organizations either issue or accept OpenIDs on their websites.
The Windows Communication Foundation (WCF), previously known as Indigo, is a free and open-source runtime and a set of APIs in the .NET Framework for building connected, service-oriented applications.
Higgins is an open-source project dedicated to giving individuals more control over their personal identity, profile and social network data.
WS-Trust is a WS-* specification and OASIS standard that provides extensions to WS-Security, specifically dealing with the issuing, renewing, and validating of security tokens, as well as with ways to establish, assess the presence of, and broker trust relationships between participants in a secure message exchange.
WS-Security Policy is a web services specification, created by IBM and 12 co-authors, that has become an OASIS standard as of version 1.2. It extends the fundamental security protocols specified by the WS-Security, WS-Trust and WS-Secure Conversation by offering mechanisms to represent the capabilities and requirements of web services as policies. Security policy assertions are based on the WS-Policy framework.
The Microsoft Open Specification Promise is a promise by Microsoft, published in September 2006, to not assert its patents, in certain conditions, against implementations of a certain list of specifications.

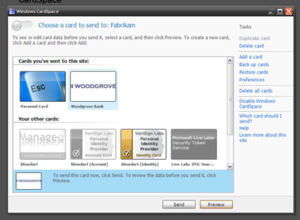
An information card is a personal digital identity that people can use online, and the key component of an identity metasystem. Visually, each i-card has a card-shaped picture and a card name associated with it that enable people to organize their digital identities and to easily select one they want to use for any given interaction. The information card metaphor has been implemented by identity selectors like Windows CardSpace, DigitalMe or Higgins Identity Selector.
Security Support Provider Interface (SSPI) is a component of Windows API that performs security-related operations such as authentication.
Active Directory Federation Services (ADFS), a software component developed by Microsoft, can run on Windows Server operating systems to provide users with single sign-on access to systems and applications located across organizational boundaries. It uses a claims-based access-control authorization model to maintain application security and to implement federated identity. Claims-based authentication involves authenticating a user based on a set of claims about that user's identity contained in a trusted token. Such a token is often issued and signed by an entity that is able to authenticate the user by other means, and that is trusted by the entity doing the claims-based authentication. It is part of the Active Directory Services. Microsoft advises using Entra ID and Azure AD Connect in place of ADFS in most cases.
Windows Identity Foundation (WIF) is a Microsoft software framework for building identity-aware applications. It provides APIs for building ASP.NET or WCF based security token services as well as tools for building claims-aware and federation capable applications.
Security token service (STS) is a cross-platform open standard core component of the OASIS group's WS-Trust web services single sign-on infrastructure framework specification.cf. Within that claims-based identity framework, a secure token service is responsible for issuing, validating, renewing and cancelling security tokens. The tokens issued by security token services can then be used to identify the holder of the token to services that adhere to the WS-Trust standard. Security token service provides the same functionality as OpenID, but unlike OpenID is not patent encumbered. Together with the rest of the WS-Trust standard, the security token service specification was initially developed by employees of IBM, Microsoft, Nortel and VeriSign.
U-Prove is a free and open-source technology and accompanying software development kit for user-centric identity management. The underlying cryptographic protocols were designed by Dr. Stefan Brands and further developed by Credentica and, subsequently, Microsoft. The technology was developed to allow internet users to disclose only the minimum amount of personal data when making electronic transactions as a way to reduce the likelihood of privacy violations.

A Microsoft account or MSA is a single sign-on personal user account for Microsoft customers to log in to consumer Microsoft services, devices running on one of Microsoft's current operating systems, and Microsoft application software.